Defenses
Introduction
Defensive systems that are primarily designed to protect civilians from the harms of war are ubiquitous. Some, like shelters, sirens, or gas masks, have been around for over a century. Walls and barriers, which have a much older pedigree, have proliferated in recent years (even if mostly to prevent immigration, not to protect from hostilities),[1] as have a host of measures grouped under the heading of “homeland security.” Other defensive measures, such as missile defense systems, were Cold War necessities that continue to be developed and deployed today by China, France, India, Israel, Italy, Japan, Russia, the United Kingdom, and the United States, as well as under the aegis of NATO.[2] Very recently, Japan has reportedly deployed missile defense systems in Tokyo to meet the threat from North Korea, as did the United States around Guam and in South Korea.[3] The United States stations additional missile defensive systems in Saudi Arabia and the United Arab Emirates. The former system was most recently implicated in missile attacks from Houthi fighters in Yemen on Riyadh. Efforts at developing tactical antimissile and antirocket defenses for shorter-range projectiles have in recent years yielded dedicated defense systems in Israel and the United States, with potential deployment in other theaters.[4] In some cases, the defenses are deployed symmetrically by both sides (e.g., the Cold War antiballistic systems), while in others, defenses are deployed asymmetrically by only one side (e.g., Israel’s Iron Dome antimissile system).
Effective defenses that protect civilians from the worst consequences of armed hostilities have significant implications for policy planning, military strategy, international relations, domestic politics, and economics. They affect policy choices with regard to political negotiations, the use of violence, military and civilian spending, and relationships with other nations. Defenses have the capacity to increase overall humanitarian welfare, although, as we shall argue here, they also run the risk of reducing it.
Though international law has very little to say specifically about defenses, its basic principles that seek to tame the use of force and to protect civilians from harm are very much relevant for defenses. They shape the legal environment in which defenses are created and deployed, the legitimacy of parties’ conduct where defenses exist, and ultimately the incentives to deploy defenses in the first place. Defenses are therefore highly relevant to the interpretation and application of the international law rules on the use of force—both the law that governs the initial resort to force (the jus ad bellum) and the law that governs the conduct of hostilities within an armed conflict (the jus in bello).
Yet, despite the significance of defenses in all these spheres, existing legal scholarship has to date focused almost exclusively on offensive action. It has, but for limited and scant exceptions, failed to analyze the effects of defensive systems on the strategic interactions between armed rivals, to consider their humanitarian consequences, or to evaluate how the interpretation and application of legal rules shape parties’ incentives to invest in defenses. The political science literature has devoted much attention to defensive systems and their tactical and strategic effects (particularly, through a strand of literature discussing the concept of “deterrence by denial”[5]), but this literature has not considered the international law dimensions. In this Article, we aim to fill these gaps.
Our framework of analysis centers on the effects of defensive systems on overall humanitarian welfare, which we define here, in accordance with the jus in bello, as the minimization of harm to civilians and civilian objects on both sides of the conflict. We do not consider other possible values, such as the justness of the parties’ causes in the armed conflict or the worthiness of the aims they are pursuing, including national self-defense, defense of others, self-determination, etc. Of course, those causes or aims could themselves increase or decrease overall humanitarian welfare, in addition to realizing (or harming) other interests. Still, our narrower framework remains faithful to the jus in bello’s focus on civilian harm, regardless of the justness of the war, and allows us a somewhat objective and generic framework for analysis.
Our focus on the overall minimization of civilian harm also allows us to engage the limited existing legal and moral philosophy scholarship that has addressed defenses. Some commentators, relying on the principle of proportionality in both the jus ad bellum and the jus in bello, have argued that by reducing the expected harm of enemy attack, defensive systems must also limit the legitimate use of force by the defenders.[6] Implicitly, these commentators seem to be motivated by the belief that such limits would better protect the lives of civilians on the enemy’s side. We argue instead that the relationship between defensive systems and the welfare of civilians is more complicated and fact-dependent. In particular, we caution against the possible disincentives that a stricter application of the principle of proportionality might generate for investments in defenses in the first place.
We begin with the simple but often overlooked observation that defenses, while designed to safeguard the lives of the population of the defending party, have the potential also to impact the lives of the opponent’s population. This is true even regardless of any legal rule. Whether their impact is entirely negative or also positive in terms of civilian welfare, however, is a much more difficult question than existing commentators seem to believe. Depending on the circumstances, defensive and offensive investments can be either strategic substitutes or strategic complements. In some cases, better defenses reduce the need for offensive action, thereby minimizing harm to civilians on enemy territory, while in others, they allow for more intense offensive actions that put such civilians at greater risk. Distinguishing between these two instances is crucial for the optimal interpretation and application of international law and, particularly, of the principle of proportionality.
Much of our focus is on the principle of proportionality in the jus ad bellum, though we also address the implications for proportionality in bello. We examine the existing weak obligation within the jus in bello to invest in defenses and consider the conditions under which we should seek to strengthen it. Beyond law, we consider possible policy implications for third parties’ intervention in armed conflicts and the benefits of intervention, in terms of overall humanitarian welfare, through the provision of defensive systems—as opposed to offensive weapons—to the warring parties.
Our analysis and results rest on a key assumption—that international law actually influences the wartime conduct of at least one of the parties to the armed conflict, and that, consequently, it also has the potential of influencing the decision whether and how much to invest in defenses. Obviously, other potentially stronger forces, such as internal political pressure or economic calculations, influence a country’s decision to invest in defenses.[7] The relative importance of international law remains an open empirical question, though we assume it is not insignificant.[8]
We divide our inquiry into cases of asymmetric defenses and symmetric defenses. In the asymmetric context, one party’s ability to defend itself far exceeds that of its rival. In symmetric conflicts, we assume respective abilities are more on par with one another. To illustrate our assumptions and analysis, we use two real-life examples of defensive systems: In the asymmetric-conflict analysis, we rely on the Israeli Iron Dome antimissile system and its potential effects on civilian welfare in the Israel–Hamas conflict. In the symmetric-conflict case, we rely on the United States’ and Soviet Union’s development and deployment of antiballistic missile defenses and the ensuing 1972 Anti-Ballistic Missile Treaty, and we also discuss the recent escalation of military tensions between North Korea and its neighbors (aided by the United States). These examples have attracted the most interest and attention in existing scholarship and commentary to date.[9]
The Article begins, in Part I, by defining the scope of the study: which defense systems we are interested in and why. Part I also describes the two specific examples of defensive systems that we subsequently use in our analysis—the Iron Dome system and the anti-intercontinental ballistic missile systems. Part II introduces the relevant international law rules that might bear on defenses, both in the jus ad bellum and the jus in bello. It includes also a summary of the scant scholarship that has addressed the relevance of defenses for these international law rules. Part III is devoted to the analytical inquiry into the effects of asymmetric defenses. It derives the privately optimal investment in defenses and compares it to the socially optimal level. The divergence between the privately optimal and socially optimal investment levels informs the legal-policy discussion. Part IV extends the analysis from the asymmetric case, where only one party to the conflict can invest substantially in defenses, to the symmetric case, where both parties can invest a great deal in defenses. Part V concludes.[10]
I. Defensive Measures
A. Definitions
National self-defense is a sufficiently broad concept to encompass and justify a wide array of strategies and tactics, ranging from diplomacy, through economic measures, all the way to active use of force. In this Article, we are interested in defenses and defensive measures that are military in their orientation, in the sense that they are designed to intercept or reduce the harm that is expected from an enemy military strike. To borrow from the political science literature, we are interested in systems that are designed to achieve deterrence by denial, that is, denying the enemy the military advantage it seeks through an attack by effectively defending against it.[11]
Defense, of course, may be passive or active: A state may build shelters for its population to protect them from air raids; it can erect barriers or fortifications around populated areas to guard against enemy military incursions; it can install early warning systems, such as sirens and alarms; it can distribute gas masks or other equipment that shield civilians from harmful fallout; or it can build more resilient structures and prepare emergency services to operate effectively in times of crisis. In all these cases, the defense is passive, in terms of its direct impact on the enemy. The state may, of course, engage in active defense in the form of preemptive or counterstrikes against enemy forces—what the political scientists deem “deterrence by punishment” to emphasize the active retaliatory action to an attack as opposed to a defensive system that seeks to frustrate the attack. Though the lines between “active” and “passive” may sometimes be blurred (as are the lines between “active defense” and “attack”), for the sake of this Article, we assume that there are enough clear cases to merit the distinction, and we focus here on passive means of self-defense. By “passive” we mean those methods that are intended to decrease the expected harm from a hostile attack without directly affecting the enemy forces or population.[12]
Moreover, we limit our inquiry to defenses that aim to safeguard the civilian population rather than the fighting forces. We thus exclude better armor, intelligence, remote war fighting, robotic platforms, etc. Clearly, defensive systems that aim to protect civilians may very well protect combatants as well (missile defensive systems are a case in point). In addition, military defense systems that aim to protect combatants may have, at the end, similar impacts on the dynamic interaction between the parties—and, therefore, on resulting casualties among civilians. Still, without excluding military defenses from our analysis it becomes increasingly difficult to distinguish between investments in defense and investments in sheer power asymmetries that allow one party to overcome its enemy with less effort and time. Moreover, as international humanitarian law (IHL) is ultimately concerned with the well-being of civilians, regulating the defense of civilians seems to fit more easily within the existing legal frameworks.
Finally, we assume that no defenses are perfectly effective. It is impossible to reduce the expected harm from enemy attacks to zero. Some risk of harm remains, to a degree that justifies engaging the enemy with military force.[13] No defense, moreover, is costless, and the costs of some defenses are significant. Both assumptions are in line with the existing defenses and conflict theaters that we are aware of, as well as the political science literature that is dedicated to defenses.[14]
B. Two Case Studies
1. The Asymmetric Case: Iron Dome—System and Data.—Iron Dome is an Israeli mobile air defense system that aims to intercept and destroy short-range rockets and artillery shells fired from a distance of between 2.5 and 43 miles (4–70 kilometers).[15] The system was designed to defend Israelis against neighboring enemies’ (mostly Hamas in Gaza and Hezbollah in Lebanon) arsenals of crude rockets and artillery shells (mostly mortar rounds), which are often labeled “statistical distribution projectiles,”[16] devoid of any guidance system other than human calculation.
The intended beneficiaries of Iron Dome are Israeli civilians, though the system undoubtedly also protects (and can be deployed specifically to protect) soldiers in Israel.[17] Iron Dome is not intended to serve as an offensive weapon and, to the best of our knowledge, has never been used in that way. It thus meets the definitional requirements outlined in subpart I(A) above.
A decades-long Israeli research and development endeavor with financial support from the United States, Iron Dome was first deployed in Israel in 2011 and made its operational debut in November 2012 during the war in Gaza (known in Israel as “Operation Pillar of Defense”) and then during the following war in Gaza in the summer of 2014 (known in Israel as “Operation Protective Edge”).[18] The reported interception success rate of the system was 84% for 2012 and 91% for 2014.[19] Though these are contested numbers, there is no dispute that the system is generally very successful.[20]
Israel is in the process of extending the effective range of Iron Dome’s interception capabilities from 43 miles to 160 miles.[21] The system itself is designed to function as only one component in a multi-tiered missile defense system, effective against both longer- and shorter-range projectiles, which is planned to become operational in the near future.[22] If successful, this multi-tiered system would reduce the threat to Israeli citizens from virtually all relevant theaters, including Iran, Syria, Lebanon, and Gaza.[23]
Over a billion dollars have already been invested in the development and deployment of Iron Dome batteries,[24] and Israeli officials announced investments of up to a billion more in expanding the number and scope of deployed systems. The estimated cost of each Tamir missile—the interceptor missile that destroys the inbound projectile—has been cited as between $30,000 and $50,000, as compared with a crudely manufactured Qassam rocket—the most common rocket fired by Hamas—which costs about $800.[25] More sophisticated Hamas rockets, such as the Grad, are more expensive, but not by much.[26] Though interception is limited to those inbound projectiles that threaten populated areas (the Tamir will not be launched if the incoming projectile does not pose a clear threat to human life[27]), the cost discrepancy between offense and defense make the system a very expensive one.[28]
The cost discrepancy[29] might also explain why Hamas (and other paramilitary factions in Gaza) has continued to launch rockets into Israel, despite the effectiveness of Iron Dome. In fact, rocket barrages from Gaza have increased in every round of large-scale clashes between Israel and Hamas since the deployment of Iron Dome.[30] Despite this increase in the number of rockets fired from Gaza, the effectiveness of the Iron Dome system ensured that the expected threat to Israelis was much lower than before the system was deployed. Of course, even the marginal threat of failed interception inflicts some real harm on the Israeli population of southern Israel, as does the continued threat of Israeli offensives on the Palestinian population in Gaza. Still, the scope and degree of harm, at least on the Israeli side, has been significantly reduced since the deployment of Iron Dome.
With the effectiveness of rocket barrages decreasing, Hamas sought to diversify its offensive tactics. The new threat comes mostly in the form of subterranean tunnels intended for the infiltration of forces and munitions into Israel. During Operation Protective Edge, dozens of such tunnels were discovered and Hamas infiltrators inside Israel killed a total of eleven Israel Defense Forces (IDF) soldiers.[31] No Israeli civilian casualties were reported, though Israeli sources claimed that at least some of the infiltrators intended to harm civilians.[32] The antimissile system thus had an effect of reducing the expected harm from rockets but potentially increasing the threat from other sources.
2. The Symmetric Case: Antiballistic Missiles.—From the late 1950s and into the 1960s, both the United States and the Soviet Union were developing antiballistic missiles (ABMs) that could intercept inbound intercontinental ballistic missiles (ICBMs) carrying nuclear warheads. Each ABM could shoot down one ICBM. Though still believed to be effective to some degree, the United States’ reliance on ABMs began to be economically infeasible as the Soviets developed an ICBM with the capacity to deliver up to ten separate warheads at a time.[33] Moreover, the upgraded ICBM delivery systems were equipped with decoys, up to forty decoys per ICBM, which would present as an actual warhead.[34] The ABM defense thus became both highly expensive and overall less effective over time.
In 1967, the United States first proposed an ABM treaty with the goal of mutually limiting the superpowers’ reliance on this mode of defense, but the Soviets rejected the proposal.[35] It was only in May 1972 that an agreement was reached to limit strategic defensive systems.[36] Under the terms of the negotiated ABM Treaty, each party was allowed to deploy ABMs in only two sites: one around its respective capital and one around ICBM silos.[37] A subsequent protocol from 1974 reduced the number of sites to one, which seemed to follow the actual practice of the parties (Moscow for the Soviet Union and North Dakota for the United States).[38] Just a few months after deploying its ABM arsenal in October 1975 as permitted under the Treaty, the United States shut down its ABM defenses because the financial costs of operating them were considered too high for the little protection they offered.[39]
In 1983, President Ronald Reagan announced the Strategic Defense Initiative (SDI, colloquially known as “Star Wars”), designed to utilize space-based antiballistic missiles.[40] Soviet leaders as well as American critics feared that the SDI would destabilize the Mutually Assured Destruction balance of power, as the United States would presumably be less vulnerable to Soviet retaliation and thus more tempted to launch a first strike. Given their already-crippled economy, the Soviets were not in a position to engage in a new arms race over space-based systems and meet the SDI with their own comparable system. Domestic opposition within the United States also criticized the initiative as being in direct violation of the 1972 ABM Treaty. By 1987, however, it became clear that the SDI could not work as a practical matter, and the program was jettisoned.[41]
In May 1999, Congress passed legislation making it the policy of the United States to deploy a limited national missile defense (NMD) system as soon as technologically possible to meet potential threats from Iran and North Korea.[42] In 2002, a few months after the September 11th, 2001, attacks, President Bush formally withdrew from the ABM Treaty after providing six-months’ notice, as required by the Treaty itself, citing other threats that the United States must defend itself from. The United States then proceeded to deploy ballistic missile defenses in Alaska and California.[43]
Other than the two Cold War protagonists, both of whom still have strategic ABM systems against ICBMs, France, Japan, India, Israel, Italy, and the United Kingdom have their own versions of ABMs (some are only effective against slower types of incoming missiles).[44] In most of these cases, the threat is symmetric, as is the ability to defend, even if one of the parties has chosen not to invest (or to invest less) in defenses.
In the past couple of years, in the shadow of a ballistic missile threat from North Korea, the United States proceeded to place ABMs in South Korea and around Guam, as did Japan around Tokyo.[45] Several members of Congress, supported by think tanks and other experts, have persistently called for greater investment in ABM systems in light of what some have called a “missile renaissance” on the contemporary battlefield.[46]
II. Defense Under International Law
Self-defense against security threats is a fundamental state right, perhaps the most important one. It is a right that is today enshrined in international legal documents, including the U.N. Charter, General Assembly resolutions, and numerous formal statements by international organizations and by individual nations.[47] It is recognized as part of customary international law, and some have characterized it as jus cogens.[48] The sovereign’s right to self-defense lies at the heart of every classical tradition as a basic natural right if not a divine scripture.[49] More modern political theory conceived of national self-defense as the very raison d’être of the nation-state,[50] and today self-defense is still offered as a justification for the persistence of the nation-state. The premise of the sovereign’s right to defend its citizens against security threats is so strong that some allude to it not only as a right but as a duty that the state owes its citizens.[51]
As earlier noted, a state might employ a range of means to protect itself from threats. International law is most concerned with self-defense that employs military force to protect against an external threat.[52] Though recognizing the inherent right of states to resort to force in the face of violent enemies, international law strives to limit the exercise of this right to the extent possible, allowing it only under strict conditions.[53] These conditions are set under both the jus ad bellum (the law that governs resort to force among states) and the jus in bello (the law that governs the conduct of hostilities once an armed conflict exists).
In this Part, we offer a brief sketch of the two legal frameworks that govern the use of force by states—the jus ad bellum and the jus in bello—and inquire whether and how they might be affected by the passive, civilian-focused defensive measures that this Article focuses on. For clarity of exposition, we distinguish between “defensive measures,” by which we refer to passive, civilian-focused defenses, and the “use of force” in self-defense, which suggests proactive strikes and other military operations against enemy forces (even if justified as a defense).
A. The Jus ad Bellum
The entire modern jus ad bellum treaty law is summed up in just three provisions in the U.N. Charter. Article 2(4) of the Charter lays down a broad prohibition on the “threat or use of force against the territorial integrity or political independence of any state.”[54] It is widely accepted that the terms “territorial integrity or political independence” were not intended to limit the prohibition in any way and that any use of force in another state’s territory, regardless of its motivation or purpose, is prima facie unlawful.[55]
Only three circumstances provide a state with legal authority to use force in the territory of another. The first, and most straightforward, is where the recognized government of a state consents to another state’s use of force in its own territory. When such consent is granted, Article 2(4) is never triggered in the first place. The other two circumstances are provided for in the U.N. Charter itself and operate as exceptions to Article 2(4). Chapter VII of the U.N. Charter entrusts the Security Council with enforcement powers in the sphere of international peace and security. The Security Council is thus empowered to authorize a state or a coalition of states to use force in another state’s territory (regardless of the territorial state’s consent) if it deems it necessary for restoring peace and security.[56] Absent consent or a Security Council authorization, the only exception to the general prohibition on the use of force is granted by Article 51 of the U.N. Charter. It recognizes states’ “inherent right of . . . self-defense” to respond to an armed attack (until such time as the Security Council has taken action).[57]
Not surprisingly, the very thin treaty law on a matter of such crucial importance for states has generated volumes of debates over each and every aspect of Article 51—its relationship to Article 2(4) and the Security Council’s powers, or its meaning and endurance in the present age more broadly.[58] Customary international law is often invoked in an aim to support different claims, though it is rarely sufficiently conclusive to resolve debates.[59]
An unusual consensus accepts that, though not specified in the text of Article 51 itself, any use of defensive force must also adhere to the customary legal requirements of necessity and proportionality.[60] These customary principles date back to the Christian Just War Theory and have been reiterated in international jurisprudence.[61] Still, whatever consensus exists with regard to the application of these principles quickly breaks down once the precise contours of each of these principles is discussed.[62]
1. Necessity.—Scholars generally agree that necessity includes the idea that there are no alternative means of redressing the situation and peaceful avenues have been tried in good faith, but to no avail.[63] This understanding of necessity echoes the Just War Theory’s requirement that war be waged only as a last resort.
Yet beyond this baseline requirement, which is often satisfied,[64] necessity analysis becomes more complicated as it is understood to include two additional possible questions. The first focuses on whether the use of force itself was necessary; the second focuses on whether the specific measures taken, or the full scope of the use of force, were necessary. Debates around the first question center on whether an initial enemy attack must meet a certain threshold of severity in order to justify an armed response or whether, once an attack takes place, necessity is satisfied and the only constraint on the response is one of proportionality.
Debates around the second question arise from the need to delineate the permissible goals of war, or, in other words, to answer the question, necessary for what? Repelling an armed invasion is an easy case;[65] thwarting an ongoing attack is similarly straightforward. Harder cases on which scholars disagree include the deterrence of future attacks, the general weakening of the enemy’s military capabilities, or even the changing of the enemy’s political leadership as a way of ensuring that the attacking party is no longer hostile.
Though little attention has been given in the literature to how necessity might be affected by states’ abilities to defend themselves better from attacks, we can construe the following analysis. For those who believe that necessity is satisfied once an attack is severe enough, defensive systems that lower the expected harm from attack would not matter that much. After all, few scholars would doubt the necessity of using force to fend off an armed invasion even if that invasion threatens only uninhabited territory. Of course, one might argue that if defense is sufficiently effective to render all enemy attacks utterly futile, the necessity to use force to preempt them would be harder to prove. And yet, no defense is costless or perfect; faced with ongoing attacks that require the employment of expensive defensive systems, a state would seem to have an easy claim of satisfying this condition.
For those who focus on the necessity of the means used to fend off the attack or preempt the threat, effective defense might affect the necessity of the use of force more directly, possibly diminishing the justification for wide-scale military operations in response to less threatening attacks. This possibility becomes clearer when we consider the second condition for the use of force—proportionality.
2. Proportionality.—The proportionality requirement, which, too, harks back to the Just War tradition, demands that the harm inflicted through force be no greater than the harm that force seeks to prevent. As Ian Brownlie, one of the first commentators on the modern formulation of ad bellum proportionality, put it, the force used must be proportionate to the threat.[66]
It follows that, just as the application of the principle of necessity requires us to agree on what the war can legitimately aim to achieve, so too does proportionality require us to agree on what harms—or threats—can be legitimately prevented through the use of force.[67] Necessity and proportionality are thus in effect intertwined and are frequently considered jointly.[68] And though proportionality often takes a more central place in debates around the use of force, it is no more clearly defined than necessity. In fact, one of the complicating facts about the assessment of proportionality is that unlike necessity, which is often thought to be determined upon the initial use of force, proportionality must be evaluated throughout the entire conflict.
For a minority of scholars, if the initial enemy attack is severe enough, self-defense allows the victim to seek the “total defeat” of the aggressor, including counter-invasion and complete destruction of the other side’s military.[69] A more common understanding of proportionality, however, demands a closer correlation between the force used and the original threat. Under this view, repelling a particular threat might entail limits on the types of weapons used, the geographical area of response, and the target of the retaliatory (or preemptory) action.[70] In some formulations of proportionality, the victim’s use of armed force is measured against the events that prompted that use of force, meaning the actual attacks the victim has suffered;[71] in others, the armed response is measured against what is needed to halt the attack or even protect against the future threat the aggressor poses.[72]
Among the many lawyers and philosophers who have debated the exact contours of the proportionality principle, very few have addressed the relevance of defensive systems. The vast majority have focused solely on the offensive side of the equation. Still, considering the various existing interpretations of the proportionality doctrine, it seems that under most views the ability of a state to defend itself against threats does affect the magnitude of that state’s legitimate use of force. More specifically, if, by definition, defensive measures reduce the resulting harm of any attack, that would implicate the proportionality condition by weakening a state’s justification to use force either to fend off or preempt future threats.
Philosopher Frances Kamm is among the few scholars who consider the implications of defenses for proportionality doctrine. Writing specifically about the Iron Dome system, Kamm has argued that Israel’s right to use force against Hamas in Gaza is substantially weakened by its ability to defend its citizens from rocket attacks.[73] She notes that the Iron Dome system provides Israel with a capability that achieves its signature goal of promoting sovereignty in a low-harm manner. Though the system is imperfect, a smaller percentage of Israelis are now at risk of harm from rocket attacks. Iron Dome has thus made the defense of only a few from attack the new military goal of Israel’s counter use of force. Kamm states that “it is relative to this ‘reduced’ goal that we would have to decide if [Palestinian] civilian casualties as a result of attacks on Gaza were proportionate.”[74] Kamm’s proportionality calculation compares the estimation of “how many Israeli civilians would be killed if the attacks on Gaza did not occur relative to the number of Gazan civilians that would be killed if the attacks occurred.” According to Kamm, “The fewer Israelis that would be saved and the more Gazan civilians that would be killed, the less likely the attack is to be proportionate.”[75]
Kamm’s argument is a philosophical one, not a legal one. Some lawyers expressed similar views, even if only in cursory terms.[76] Other commentators, though not rebutting Kamm’s proportionality claim per se, would place greater emphasis on Israel’s right to defend itself, its duty to defend its citizens, the fact that the Iron Dome system is imperfect, and the argument that military force is still necessary and justified to preempt further attacks.[77] Whatever the precise weight to be assigned to each of these considerations, and without fully endorsing Kamm’s position, it seems to us safe to conclude that effective defensive systems do affect to some degree the proportionality calculation of a state’s legitimate use of force in self-defense as a matter of international law.
It is also worth noting that, whether or not accurate as a matter of international law, Kamm’s position certainly captured the political reality around Iron Dome: As one RAND Corporation researcher put it, “Successful missile defense shifted the international political response to the conflict. In both Pillar of Defense [the Israeli–Hamas war that preceded Protective Edge] and Protective Edge, the largely unharmed Israeli population contrasted sharply with media images of destruction in Gaza, bringing about increased international condemnation.”[78]
B. The Jus in Bello
Under the traditional and prevailing view, IHL applies in any case of war, independently from the justification of the war to begin with. It could thus apply to both defensive wars as well as to wars of aggression. The stated purpose of IHL is to mitigate war’s harmful effects, while still conceding its realities. Conventionally stated, it is to mediate between military necessity and humanitarian considerations.
With its primary concern being the harms wrought by war, the vast majority of IHL provisions address parties’ conduct that is directed against enemy forces and populations. Such provisions include limits on the types of weapons that parties may employ, obligations to distinguish military from civilian targets, the need to take precautions in attacks in order to minimize collateral harm to civilians and civilian objects, the duty to respect the inviolability of medical teams that attend to the sick and wounded, positive and negative duties with regard to prisoners of war or enemy civilians, and more.[79] The driving assumption behind these rules is that, left to their own devices, warring parties are likely to inflict a great deal of suffering on enemy forces and civilians, much of which is unnecessary or unjustified, and that the impetus to hurt the enemy must be checked by law.
In contrast, the law does not assume any malevolence by a leadership towards its own constituency that needs to be checked or corrected against. For that reason, IHL has little to say about how a warring party treats its own people, whether combatants or civilians. That set of obligations is left, instead, to international human rights laws (or their domestic law incarnation) that impose obligations on governments with regard to their own citizens. Where IHL does include obligations that pertain to a party’s own forces, these obligations are largely meant to allow the adversary to fight lawfully, without inflicting excessive harm on civilians. For example, belligerent forces are under an obligation to identify themselves through uniform or other distinctive insignia so as to enable enemy forces to comply with their obligation to direct their attacks only against combatants.[80]
1. Obligation to Defend the Local Population.—It is an exceptional case where IHL instructs parties on the defense of their own forces or civilians. The only relevant treaty provision is found in Article 58 of the 1977 Additional Protocol I (API),[81] which states:
The Parties to the conflict shall, to the maximum extent feasible:
(a) Without prejudice to Article 49 of the Fourth Convention, endeavour to remove the civilian population, individual civilians and civilian objects under their control from the vicinity of military objectives;
(b) Avoid locating military objectives within or near densely populated areas;
(c) Take the other necessary precautions to protect the civilian population, individual civilians and civilian objects under their control against the dangers resulting from military operations.[82]
The 1987 Official Commentary to Additional Protocol I explains, “From the beginning of its work the [International Committee of the Red Cross] has felt the need to lay down provisions for ‘passive’ precautions, apart from active precautions, if the civilian population is to be adequately protected.”[83] The Commentary notes also that “during the final debate several delegations indicated that in the view of their governments, this article should in no way affect the freedom of a State Party to the Protocol to organize its national defence to the best of its ability and in the most effective way.”[84] As explained by the Commentary, one reason why the duty to employ passive precautions made it into the Additional Protocol is that such passive precautions are in a state’s own interest.[85] Thus, the Commentary notes, “Belligerents may expect their adversaries to conduct themselves fully in accordance with their treaty obligations and to respect the civilian population, but they themselves must also cooperate by taking all possible precautions for the benefit of their own population as is in any case in their own interest.”[86] Nowhere does the Commentary suggest that defense might have humanitarian benefits, however indirectly, for the enemy population as well, and it seems that this possibility was never on the minds of the drafters of the Additional Protocol.
Article 58 has been and remains today an obscure IHL obligation, one that has not attracted the attention of scholars, courts, or practitioners. The limited importance that seems to be attached to it derives, we believe, precisely from the Commentary’s assumption that rational actors who can afford defenses would employ them regardless of any treaty obligation. This assumption, as we argue later, is not necessarily correct: one could imagine a range of instances in which parties’ leaders would not wish to invest in the defense of their population. Leaders might be indifferent to the fate of their own citizens, believe that civilian casualties serve their political or strategic interests, or else prefer to invest their resources in offensive capability rather than in defense as a matter of military strategy. To the extent that adherence to international law might affect these leaders’ choice, it is unfortunate that Article 58 has not received more attention in advocacy, practice, or scholarship. At the same time, as we show later in this Article, defenses might sometimes adversely affect civilians on the enemy side. In these cases, a strict obligation under Article 58 would be at odds with the goal of promoting overall humanitarian welfare.
2. In Bello Proportionality.—Apart from any direct reference in the law to the deployment of defensive means, some international law scholars believe that defense implicates IHL in at least one more important way: the jus in bello principle of proportionality. This principle dictates that, while directing attacks against legitimate military targets, parties may inflict some collateral damage on civilians and civilian targets, so long as that damage is unintentional and is not excessive in relation to the military advantage that is anticipated by the attack.[87] The principle of proportionality is complemented by an affirmative duty on the attacker to employ all feasible precautions in order to minimize harm to civilians and civilian objects in the course of military operations.[88]
Weighing military advantage against civilian lives and property is an enduring practical and conceptual challenge. The incommensurability of the relevant values coupled with the subjectivity of the assessment are but two complicating factors. The voluminous scholarship on proportionality has debated the degree to which soldiers’ lives should be factored into the assessment of military advantage and whether or not soldiers must assume more risk to themselves in order to minimize the risk to enemy civilians from collateral damage (debates over so-called force protection).[89] In contrast, existing scholarship has paid far less attention to the threat to civilians on the attacker’s side and how such threat should affect the military advantage against which any collateral harm to enemy civilians must be weighed.
Here, too, Iron Dome has drawn out some exceptions. In analyzing the implications of Iron Dome for in bello proportionality, Michael Schmitt and John Merriam argue that defensive capacities do entail some decrease in the “degree of terror . . . with improved defenses and that, accordingly, the military advantage of striking a rocket does diminish somewhat as the effectiveness of defenses increases.”[90] The corollary decrease in permissible collateral damage, however, is not substantial in their minds. The authors quote three reasons for keeping any effect of defensive systems on proportionality analysis small: First, they claim that there is an inherent military value in the destruction of rocket launchers and other enemy offensive weaponry, regardless of improved defenses. Second, they claim that a state’s efforts and expenditures in defensive capabilities “should not undermine its ability to diminish its adversary’s offensive capabilities.”[91] And third, the authors claim that the rocket barrages against Israel are aimed at terrorizing the population and that a 95% reduction in the rockets’ impact rate may not necessarily cause a 95% reduction in their terrorizing effect.[92] In response, Amichai Cohen and Yuval Shany counter that the highly effective Iron Dome system decreases the necessity of and the concrete military advantage deriving from neutralizing rocket attacks, and thus limits military action under the principle of proportionality.[93]
While we are sympathetic to Cohen and Shany’s intuitions, we would caution against conflating in bello with ad bellum proportionality. It is the case, we believe, that in particular engagements where the military advantage being sought in attacking the enemy is designed to immediately protect the civilian population (for instance, firing at militants who are aiming their weapons at civilians), defensive systems that already protect the civilian population diminish that military advantage, and as a corollary, also diminish permissible collateral damage. It does not follow, however, that in each engagement with enemy forces the military advantage is willy-nilly diminished on account of effective civilian defenses; in that sense, we think Schmitt and Merriam are correct in arguing that in bello military advantage is derived from diminishing the enemy’s numbers and capabilities independently of the immediate threat it poses. The broader necessity and proportionality calculations of how much to engage the enemy—or how much military advantage could be sought—belong in the ad bellum analysis.
Still, what is indisputable is that defensive systems would affect proportionality in bello at least to some extent. Moreover, even if one were to accept the argument that defenses should not impact—or not impact by much—the legitimacy of counter military action as a matter of in bello proportionality, it might still affect the jus ad bellum proportionality. Both notions of proportionality reflect the idea that one party’s investment in defenses protects, or should protect, civilian lives on the other side of the conflict. Our inquiry must therefore examine how this application of the principle of proportionality—an application that leads to greater constraints on military action—affects the incentive to invest in defense in the first place.[94]
III. A Consequentialist Theory of Defenses: Asymmetric Defenses
We develop a consequentialist theory of defenses and use it to assess the full implications of the international law rules described above as well as any possible policy derivatives. This Part focuses on asymmetric defenses, namely on the case where only one party may invest in defensive measures.[95] We refer to the party who may invest in defenses as “Party A” (or simply “A”). We refer to the other party as “Party B” (or simply “B”).
A. The Basic Argument
1. Defenses Create Externalities.—Our goal is to explicate the effects of international law on the combatting parties and on overall social welfare. But first we must understand the basic structure of the strategic interaction and the role that defenses play. The defending party, Party A, will invest in defenses if the investment serves A’s interests. The question is whether A’s defenses harm or, rather, help the attacking party, Party B. In economic terms, does A’s investment in defenses create a negative externality or a positive externality? If defenses create a negative externality, then A would be expected to invest too much in defenses, from a social welfare perspective, and—to the degree that international law seeks to minimize civilian harm[96]—the law should aim to curb these excessive investments. On the other hand, if defenses create a positive externality, then A would be expected to invest too little in defenses and the law should encourage further investment. We show that under certain conditions, which we identify, defenses create a negative externality; and that under other conditions, which we also identify, defenses create a positive externality.
We begin with the negative-externality conditions. When two parties are at war, investments by one party would generally be designed to help the investing party and hurt its adversary. After all, war is often a zero-sum game. Indeed, in the most basic setup, A’s defenses hurt B: they make it more difficult for B to achieve its goal of harming A (this is the logic behind the term “deterrence by denial”[97]). Moreover, A’s defenses create a quasi-immunity against retaliation by B, and thus allow A to launch more harmful attacks against B. Defensive and offensive investments are complements. We see that A’s investment in defenses can hurt B—namely, defenses can create a negative externality.
But defenses can also create a positive externality. As A enjoys better defenses, it might be less compelled to rely on offensive actions, thereby decreasing the expected harm to B’s civilians. (Note that even the most discriminate military action directed against legitimate targets is liable to inflict some collateral harm on B’s civilians, given populated battlegrounds.) We thus identify a substitution effect between A’s offensive and defensive investments.
The positive-externality argument, supported by the substitution effect, relies on the existence of an agency problem on B’s side.[98] The claim, which we consider quite plausible, is that B’s government or military decision makers do not fully internalize the interests of B’s civilian population. When this is the case, A’s defenses harm the interests of B’s government or military decision makers, but help B’s civilians. Alternatively, the leadership and population of B share a similar set of interests, but those go beyond the protection of civilian lives (e.g., self-determination). In this case, defenses, while harming the broader interests of B, might nevertheless promote the IHL goal of protecting civilian lives in conflict situations.
2. The Ex Ante Effects of International Law.—We now turn back to international law and consider its effects on Party A, Party B, and overall humanitarian welfare. In order to gauge the effects of the law, we assume that at least one of the parties complies with the law.[99] As before, we assume that international law seeks to constrain military action so as to protect civilians.[100] It does so, in part, through the principle of proportionality. This principle constrains A’s ability to engage in offensive action and thus helps B. From an ex post perspective, therefore, international law provides a clear benefit to B’s civilians.
But the ex post perspective is too narrow. We must also consider the ex ante effects of the law. A stricter proportionality principle, by limiting A’s offensive actions, weakens A’s ability to deter B, possibly resulting in more intensive attacks by B.[101] These more intensive attacks will lead to harsher retaliation by A—to the detriment of B’s civilians. In the absence of defenses, these ex ante effects undermine (and potentially outweigh) the ex post benefit of the proportionality principle.
Defenses can mute the ex ante effects. By increasing the threat that A faces, the ex ante effects push A to take stronger offensive action. When A has defenses in place, those defenses reduce the threat A faces and thus provide a substitute for offensive action. Thus, A’s defenses can help B’s civilians. If international law effectively “punishes” A for its investments in defense by demanding a stricter proportionality analysis, A might be deterred from investing in defenses in the first place—an investment that helps not only A, but also B’s civilians. We therefore suggest an interpretation and application of the proportionality principle that seeks to avoid these adverse consequences.
The preceding argument focuses on the positive-externality case. In that case, the concern is about insufficient investment in defenses, and so the law should be designed to encourage such investment. The opposite is true in the negative-externality case. In that case, the concern is about excessive investment in defenses that shield A from the effects of retaliation and thus invite A to launch more intense attacks against B. The law mitigates this problem: by imposing limits on A’s attacks, the proportionality doctrine constrains A’s offensive action and thus reduces the value, to A, of defenses and, accordingly, the incentive to invest in defenses in the first place.
We now develop and refine this basic argument. We begin by describing, in greater detail, our framework of analysis.
B. Framework of Analysis
1. Setup.—There are two parties, Party A and Party B, engaged in an armed conflict. There are three time periods.[102] At T0, Party A chooses how much to invest in defenses. We assume that a party’s investment in defenses affects the harm that this party will suffer if the other party attacks. Specifically, we assume that a greater investment in defenses reduces the harm. For example, Israel’s investment in Iron Dome reduced the number of civilian casualties from Hamas rockets.
For the remaining time periods, we distinguish between, and separately analyze, two scenarios (which are not mutually exclusive). The difference between the two scenarios has to do with the order of attacks—which party attacks first and which party attacks second. In particular, Scenario 1 is defined as follows: at T1, Party B launches an attack and chooses the intensity—namely, the probability and severity—of this attack; at T2, Party A launches an attack and chooses the intensity of this attack. And Scenario 2 is defined as follows: at T1, Party A launches an attack and chooses the intensity of this attack; at T2, Party B launches an attack and chooses the intensity of this attack. In reality, parties are often engaged in multiple rounds of attacks and counterattacks, such that each party can be seen as both attacking first and attacking second. Still, it is analytically useful to distinguish between the two scenarios.
The attacks generate a benefit to the attacking party and a harm to the attacked party. The harm component is straightforward: a more intense attack inflicts greater harm on the attacked party. Also, as noted above, for Party A, a greater investment in defenses reduces the harm incurred (for any level of attack intensity).
Next consider the benefit to the attacking party. When A attacks B, A receives a benefit that increases with the harm incurred by B, reflecting the idea that your opponent’s harm is your gain, e.g., since a weakened opponent is less able to attack. This benefit component applies in both Scenario 1, where B attacks first, and in Scenario 2, where A attacks first. There is a second benefit component that A obtains only in Scenario 1, where A attacks at T2 in retaliation to B’s T1 attack. In this scenario, A receives an additional benefit from harming B at T2 in proportion to the harm that A suffered from B’s attack at T1. This second benefit component reflects the idea that when A suffers greater harm from B’s T1 attack, A would like to retaliate by inflicting greater harm on B at T2.[103] The benefit to B from attacking A can be similarly divided into these two components.
We begin the analysis assuming that Party A and Party B are unitary actors. Yet, in some cases, important agency problems merit a distinction between a party’s military or political leadership and its civilian population. We thus distinguish between the harm (or benefit) to A’s military and the harm (or benefit) to A’s civilian population—and similarly for B. The agency problem arises when decisions about attacking and defending are made by the military (or by a government allied with the military) without fully considering the interests of the civilian population.[104]
Alternatively, we could maintain the assumption that Party A and Party B are unitary actors but acknowledge that the common interests of these unitary actors go beyond the protection of civilians. For example, Party A—both A’s military or political leadership and A’s civilian population—may care about protecting the state’s sovereignty, even when it puts civilians at risk. This does not mean that Party A does not care about civilian casualties, only that other goals may dominate. In this alternative specification, we distinguish between the interests of the unitary Party A and the objectives of international humanitarian law, which focuses on the protection of civilians[105]—and similarly for Party B.
2. Private- and Social-Objective Functions.—We now specify the private-objective functions—of Party A and Party B—as well as the social-objective function. The private-objective functions are crucial to understanding the choices of both offensive and defensive operations that the two parties make. The social-objective function will guide our normative assessment of the parties’ choices and the potential role of international law. There are ongoing debates about what the parties’ private objectives are and about what the social objective should be. We try to avoid taking sides in these debates. Rather, we will attempt to consider several possible private- and social-objective functions and explore whether and how the analysis depends on these variations.
We assume that Party B seeks to maximize the benefit from harming A minus (i) the expected harm to B from A’s attack and (ii) the cost to B of attacking. Similarly, we assume that Party A seeks to maximize the benefit from harming B minus (i) the expected harm to A from B’s attack, (ii) the cost to A of attacking, and (iii) the cost to A of investment in defensive measures. This third cost component constitutes the only structural difference between the two parties’ objective functions, and it reflects the context of asymmetric defenses. There could be other differences: the benefit and harm functions can be different for Party A and Party B. And the cost of attacking could also be different. For example, one party may care more about protecting civilians on the other side and, correspondingly, enjoy a smaller benefit from attacking the other party.[106] We consider different specifications for the benefit, harm, and costs to Party A and Party B or, more generally, different specifications for the parties’ private-objective functions and explore how the different specifications affect the analysis.
We next consider the social-welfare function. A standard approach is to define the social-welfare function as a combination of the two parties’ objective functions. When agency problems are severe, we will separately consider the objectives of the parties’ civilian populations. In the present context, the international legal rules are concerned with the welfare of the civilian populations, and so we will focus on this objective.
The disparity between the parties’ private-objective functions and the social-objective function foreshadows the loss that occurs in the absence of legal intervention. Party B chooses the intensity of its attack in a way that maximizes Party B’s private-objective function; it does not consider the effects of its choice on Party A’s objectives or on the overall social welfare. Similarly, Party A chooses the intensity of its attack and the amount it invests in defenses in a way that maximizes Party A’s private-objective function; it does not consider the effects of its choice on Party B’s objectives or on the overall social welfare. Since each party’s decisions also affect the other party, and since these externalities are not accounted for by the decision maker, we can expect welfare-reducing decisions. International law can help correct the suboptimal incentives.[107]
C. Scenario 1: Party B Attacks First
We start with Scenario 1, where Party B attacks at T1 and Party A attacks at T2. We solve the extensive form game by backward induction; namely, we first analyze the last period, T2, then go back and analyze T1, and finally reach T0.[108] We are interested primarily in A’s T0 investment in defenses. Therefore, as we proceed by backward induction, we focus on the effects of defenses on the T1 and T2 choices.
1. T2: Party A Attacks.—At T2, Party A chooses the intensity of its attack. A more intense T2 attack increases the harm to B, which benefits A. More importantly, for present purposes, the intensity of A’s T2 attack increases with the harm to A from B’s T1 attack because of the retaliation component (namely, when B’s T1 attack is more harmful, A would want to launch a more intense T2 attack). Therefore, the intensity of A’s T2 attack increases with the intensity of B’s T1 attack and decreases with the strength of A’s defenses. We obtain a substitution effect: greater investment in defense results in less intense retaliation.
2. T1: Party B Attacks.—At T1, Party B chooses the intensity of its attack. There are three forces at play. First, a more intense T1 attack causes more harm to A, which benefits B. This effect pushes for a more intense T1 attack. Second, a more intense T1 attack might lead to a more intense T2 retaliatory attack by Party A. This deterrence effect pushes B to launch a less intense T1 attack. Third, launching an attack is costly to B, which also pushes B to launch a less intense attack. Party B weighs these three effects when deciding on the intensity of its T1 attack.
Defenses affect B’s decision through two different channels: First, better defenses reduce the efficiency of B’s attack, thus reducing the intensity of B’s T1 attack. (When the returns from an investment are smaller, a rational party will invest less.) Second, better defenses reduce the harm to A from B’s T1 attack and thus reduce the intensity of A’s T2 retaliatory attack;[109] this results in reduced deterrence and thus increases the intensity of B’s T1 attack. When the efficiency effect dominates, better defenses reduce the intensity of B’s T1 attack. When the deterrence effect dominates, better defenses increase the intensity of B’s T1 attack.[110]
3. T0: Party A Invests in Defenses.—We can now analyze A’s decision to invest in defensive measures. We begin with the direct effect of defenses: stronger defenses result in less harm from B’s T1 attack and thus help A. This direct effect pushes towards greater investment in defenses. In addition, A’s defenses also affect the intensity of B’s T1 attack and thus, indirectly, the harm incurred by A (section III(c)(2) above). If A’s defenses reduce the intensity of B’s T1 attack, then this indirect effect joins the direct effect, and defenses clearly help A. Party A will balance these two benefits of investment in defenses against the cost of such investment and decide on the (privately) optimal level of investment. However, if A’s defenses increase the intensity of B’s T1 attack, then the indirect effect counters the direct effect. When the direct effect dominates, defenses are overall beneficial, and A will balance this benefit against the cost of the defense and decide on the (privately) optimal level of investment. When the indirect effect dominates, defenses are overall harmful to A, so A will not invest in defenses.
4. Effect of A’s Defenses on B.—Do A’s defenses help B or rather hurt B? In other words, do defenses create a positive externality or a negative externality? The effect of A’s defenses on B is critical to our normative analysis. Party A considers the effect of defenses on A but, absent legal intervention, does not consider the effect of defenses on B.[111] Therefore, if defenses create a positive externality, then A will invest too little in defenses; and if defenses create a negative externality, then A will invest too much in defenses. This will be the normative assessment if we view the social-welfare function as a simple aggregate of the parties’ private-objective functions. And, as we will soon see, this will also be the normative assessment if our social objective is to minimize civilian casualties.
We begin with the assumption that both A and B are unitary actors, namely that A’s government or military decision makers are perfectly faithful agents of A’s civilian population and that B’s government or military decision makers are perfectly faithful agents of B’s civilian population. Under these assumptions, A’s defenses clearly hurt B. Specifically, A’s defenses hurt B by reducing the harm that B can inflict on A (recall that B benefits from harming A). We have a negative externality, which means that A will invest too much in defenses from a social-welfare perspective.
Now consider the implications of agency problems on B’s side. What happens when B’s government or military decision makers are not perfectly faithful agents of B’s civilian population? If B’s decision makers, in choosing the intensity of B’s T1 attack, do not fully internalize the harm to B’s civilians, then A’s defenses can help B’s civilian population. In particular, when better defenses reduce the intensity of B’s T1 attack, they will also reduce the intensity of A’s T2 retaliatory attack, thus helping B’s civilians. The introduction of an agency problem transforms a negative-externality result into a positive-externality result. If we view the social-welfare function as an aggregate of the private-objective functions of the two parties’ civilian populations, then A will invest too little in defenses. Similarly, if we adopt the IHL social-objective function that seeks to minimize overall civilian casualties, then the positive-externality result implies that A will invest too little in defenses.
5. The Law.—Focusing on the proportionality doctrine, we conceptualize the law as a limit on A’s T2 retaliatory attack. The law imposes a constraint on the relationship between the harm that B’s T1 attack inflicts on A and the harm that A can inflict on B through its T2 retaliatory attack. More specifically, if the harm that B inflicted on A is , then the harm that A can inflict on B, , cannot exceed , where l represents the legal standard. Put differently, the ratio between and cannot exceed l:
.
There is a legal, doctrinal question about how to apply the proportionality doctrine when one party invests in defenses. According to our understanding of how the common interpretation of the proportionality doctrine would view defenses (recall, Kamm is the only scholar who addresses this question head-on[112]), when applying the formula, we should consider the expected harm to A, given A’s investment in defenses: . We call this the “standard interpretation,” even though “standard” may be an overstatement. As we will see, this interpretation might provide an insufficient incentive for A to invest in defenses. We thus propose that, in the positive-externalities case, defenses will not be taken into account, at least not fully, when applying the proportionality doctrine. Specifically, according to our new interpretation of proportionality, permissible retaliation is defined relative to a “no defenses” benchmark: , where “no defenses” (or “without defenses”) should be understood as shorthand for taking less-than-full account of the effect of defenses, and not necessarily for not counting defenses at all.
Starting with the standard interpretation: the main effect of the law is to constrain A’s T2 retaliatory attack. Since the law reduces B’s concern about A’s T2 retaliatory attack, B will launch a more intense T1 attack. Anticipating the more intense T1 attack, A will invest more in defenses at T0. While a stricter law provides an extra incentive for A to invest in defenses, there is a countervailing reason, we have seen, why A might be reluctant to invest in defenses: this investment reduces the deterrence effect—stronger defenses reduce the harm to A and thus reduce the intensity of A’s legally permissible T2 retaliatory attack. This reduced deterrence induces a more intense T1 attack by B and thus hurts A. Put differently, A understands that better defenses, by reducing (though not eliminating) the harm it incurs, further constrain its ability to take offensive action, and this understanding might reduce A’s investment in defenses.
With our proposed interpretation of proportionality, A’s investment in defenses does not have this adverse deterrence-reducing effect. When, following the standard interpretation, proportionality is measured vis-à-vis a “with defenses” benchmark, the law “punishes” A for its investment in defenses, tightening the legal constraint and reducing the deterrence effect. When, following our proposed interpretation, proportionality is measured vis-à-vis a “without defenses” benchmark, A’s investment in defenses does not affect the legal constraint and thus does not further reduce the deterrence effect. Therefore, A will invest more in defenses under our proposed interpretation. This is a socially desirable outcome when A’s defenses create a positive externality.
To elaborate, taking the level of defenses as given, a stricter proportionality doctrine helps B’s civilians by constraining A’s T2 retaliatory attack. But, of course, we cannot take the level of defenses as given. Specifically, under the standard interpretation, a stricter law might result in a suboptimal investment in defenses. With weaker defenses, A will incur more harm (this would be true even where B’s attacks are within what the law allows). And when A incurs more harm, the law will allow A to inflict more harm on B, and also on B’s civilian population. Therefore, we can help B’s civilians by adopting our proposed interpretation of proportionality doctrine, which provides stronger incentives for A to invest in defenses.[113]
But even this revised understanding of proportionality might not provide sufficient incentives to invest in defenses. To further increase investment in defenses, we may want to consider a legal duty to defend, or, to use existing law, take Article 58 of API more seriously. And looking beyond the law, other countries or international organizations can subsidize A’s investment in defense or directly invest in A’s defenses, as the United States did with Iron Dome.
D. Scenario 2: Party A Attacks First
We now consider Scenario 2, where Party A attacks at T1 and Party B retaliates at T2. Again, we solve the extensive form game by backward induction; namely, we first analyze the last period, T2, then go back and analyze T1, and finally reach T0.
1. T2: Party B Attacks.—At T2, Party B chooses the intensity of its retaliation. A more intense T2 retaliation increases the harm to A, which benefits B. The intensity of B’s T2 retaliation increases with the intensity of A’s T1 attack and the harm suffered by B as a result. More importantly for present purposes, the intensity of B’s T2 retaliation decreases with the quality of A’s defenses. When A has better defenses, the harm to A is smaller, the efficacy of B’s retaliation is smaller, and thus B will choose a less intense T2 attack.
2. T1: Party A Attacks.—At T1, Party A chooses the intensity of its attack. There are three forces at play. First, a more intense T1 attack causes more harm to B, which benefits A. This effect pushes for a more intense T1 attack. Second, a more intense T1 attack might lead to a more intense T2 retaliatory attack by Party B. This deterrence effect pushes A to launch a less intense T1 attack. Third, launching an attack is costly to A, which also pushes A to launch a less intense attack. Party A weighs these three effects when deciding on the intensity of its T1 attack.
A’s defenses increase the intensity of A’s T1 attack: Better defenses reduce the efficiency of B’s T2 retaliation and thus reduce its intensity. Specifically, A’s defenses reduce the deterrence effect (from B’s anticipated T2 retaliation, which increases with the harm to B from A’s T1 attack) and thus increase the intensity of A’s T1 attack.
3. T0: Party A Invests in Defenses.—We can now analyze A’s decision to invest in defensive measures. In Scenario 2, we have only the direct effect: stronger defenses result in less harm from B’s T2 attack and thus help A. This direct effect pushes towards greater investment in defenses. A will balance this benefit of investment in defenses against the cost of such investment and decide on the (privately) optimal level of investment.
4. Effect of A’s Defenses on B.—Do A’s defenses help B or rather hurt B? We begin with the assumption that both A and B are unitary actors, namely that A’s government or military decision makers are perfectly faithful agents of A’s civilian population, and that B’s government or military decision makers are perfectly faithful agents of B’s civilian population. Under these assumptions, A’s defenses clearly hurt B. Specifically, A’s defenses hurt B by reducing the harm that B can inflict on A (recall that B benefits from harming A). In addition, A’s defenses increase the intensity of A’s T1 attack and thus the harm to B from this attack. We have a negative externality, which means that A will invest too much in defenses from a social-welfare perspective.
Now consider the implications of agency problems on B’s side. What happens when B’s government or military decision makers are not perfectly faithful agents of B’s civilian population? Specifically, what happens if B’s decision makers, in choosing the intensity of B’s T1 attack, do not fully internalize the harm to B’s civilians? In Scenario 2, agency problems do not change the basic result. A’s defenses hurt B’s civilians by increasing the intensity of A’s T1 attack and thus the harm to B’s civilians from this attack. As in the unitary actors case, here too defenses create a negative externality, which means that A will invest too much in defenses from a social-welfare perspective and from the perspective of IHL.
5. The Law.—How should we think about the proportionality doctrine, especially as it applies to A, when A attacks first? According to international law, A’s T1 attack must be proportional to any threat from B’s T2 attack.[114] The intensity of B’s T2 attack, and thus the harm to A from such an attack, has two components: (1) a level of attack intensity that B would choose at T2 even if A did not attack at T1 and (2) an additional degree of attack intensity that responds to (or is chosen in retaliation to) A’s T1 attack. For purposes of the proportionality doctrine, we should consider only the first component (it seems less plausible to consider expected T2 harm to A that would not have occurred if A did not attack at T1). Consider the following example: if A did not attack at T1, then at T2, B would attack at an intensity that inflicts 100 casualties on A. And if A attacks at T1, then at T2, B would attack at an intensity that inflicts 200 casualties on A. The benchmark harm, for purposes of the proportionality doctrine, is 100 casualties, not 200 casualties.
Defenses help A by reducing the harm from B’s T2 attack. A stricter law reduces the intensity of A’s T1 attack and thus reduces the intensity of B’s T2 retaliatory attack and the harm to A from that attack. Therefore, there is less need for defenses. The weaker incentive to invest in defenses is socially desirable, since defenses create a negative externality.
The preceding analysis follows the standard interpretation of proportionality doctrine (as defined in section III(C)(5) above). According to the standard interpretation, proportionality doctrine reduces A’s incentive to invest in defenses, which is desirable in Scenario 2, where defenses create a negative externality. Therefore, here we do not need to consider any alternative interpretation of proportionality.
E. Taking Stock
In Scenario 1, defenses create a positive externality and need to be encouraged. The proportionality doctrine does so, and it does so more effectively with our proposed new interpretation that does not take fully into account a party’s defenses in balancing the permissible use of force against the threat posed by the enemy. In Scenario 2, defenses create a negative externality and need to be discouraged. The standard interpretation of the proportionality doctrine does so, and our proposed interpretation would be counterproductive. This creates a problem for policymakers, especially since the two scenarios are not mutually exclusive; indeed, each scenario represents one aspect of what is often a complex, multi-round conflict.
Still, our analysis can provide some guidance regarding the optimal interpretation of the proportionality doctrine. In certain conflicts, the positive-externality feature is dominant and then our proposed interpretation should be adopted. In other conflicts, the negative-externality feature dominates and then the standard interpretation should be used. To identify the dominant externality, lawmakers should ask the following key question: In the particular conflict, and for the particular Party A, are defensive and offensive investments substitutes or complements? If they are substitutes, then we are in the positive-externality case and our new interpretation of proportionality should be preferred. If they are complements, then we are in the negative-externality case and the standard interpretation of proportionality should be preferred.
IV. Asymmetric Defenses—Extensions and Applications
A. The Marginal Cost of Defenses
We are interested in defenses and in the role that international law plays in encouraging or discouraging investment in defenses. The cost of such an investment can be roughly divided into two components—a fixed-cost component, which includes research and development (R&D) investments and the costs of long-term equipment (such as radar systems), and a marginal-cost component, which includes costs that are incurred each time the defensive system needs to be activated (e.g., the cost of the intercepting missile that destroys an incoming projectile). Our analysis thus far has focused, implicitly, on the fixed-cost component. We now consider the implications of the marginal cost of defenses.
First, a high marginal cost of defenses gives the other party a new way to harm the defender. Even if the defensive system is effective in preventing civilian casualties, Party B can impose substantial financial costs on Party A by, for instance, firing many rockets and forcing Party A to expend substantial resources in intercepting them. The high marginal cost of defenses can thus be expected to increase the intensity of B’s attack. On A’s part, the high costs of defense might deter investment altogether or drive A to invest only in defenses that have a lower marginal cost.
From a normative perspective, the large marginal cost, while helping B, may well hurt civilians on both sides (especially in the positive-externality case). The more intense attack by B might trigger more intense retaliation by A, which might hurt B’s civilian population. Also, if the large marginal cost causes A to invest less in defenses, then a larger number of casualties for A might trigger more intense retaliation, again hurting B’s civilians. The effect of international law remains qualitatively unchanged. In particular, a stricter proportionality doctrine might hurt, rather than help, civilians.
B. Bounded Rationality
We have thus far assumed that decision makers, Party A and Party B, are perfectly rational. How does the analysis change when we relax the rationality assumption? Consider Scenario 1. Focusing on B’s decision to launch a T1 attack, the rationality assumption played a crucial role in deriving the relationship between A’s investment in defenses and the intensity of B’s T1 attack. Better defenses, we argued, reduce the efficacy of B’s T1 attack, and thus a rational Party B would be expected to reduce the intensity of its attack.
This prediction needs to be revisited if Party B is boundedly rational. Consider, for example, one prominent account of bounded rationality—Herbert Simon’s satisficing theory. According to this theory, a decision maker sets a certain “satisfactory” goal and proceeds with the activity until this goal is reached.[115] In our framework, Party B may set a goal, explicitly or implicitly, of inflicting a certain level of harm on Party A, and thus continue to fire rockets until this goal is reached. If B “satisfices” in this manner, then better defenses can be expected to increase—not decrease—the intensity of B’s T1 attack.
Also note that, in this satisficing model, the harm to A is independent of A’s investment in defenses, which means that A will have no reason to invest in defenses in the first place. This also means that international law will have no effect on A’s investment in defenses. Of course, a pure satisficing model seems unrealistic. Rather, Party B’s decision-making likely reflects some hybrid combination of rational calculation and satisficing.
The preceding discussion focused on Party B’s bounded rationality. What are the implications of bounded rationality on A’s side? For example, what happens if a boundedly rational A considers the high present costs of investing in defenses but underestimates the even larger future benefits, to A, of defenses. Such myopia, or present bias, would reduce the investment in defenses, which would be harmful in the positive-externality case, but helpful in the negative-externality case.
C. Targeting a Rival’s Offensive Capabilities
The framework of analysis in Part III provided limited details on the source of the benefit that a party gets from attacking its rival. We now consider one particular source of benefit—reducing the rival’s offensive capabilities as a means of protecting against future attacks by this rival. Focus on Party B, and assume that B attacks A in order to reduce A’s offensive capabilities. As before, A’s defenses reduce the efficacy of B’s attack—this time by making it harder for B to reduce A’s offensive capabilities.
More interestingly, when B’s motive is to reduce A’s offensive capabilities, there is a new externality that should be considered: A’s investment in defenses helps B by substituting for B’s investment in better, more accurate offensive systems. Assume that B does not wish to harm A’s civilians, but only to reduce A’s offensive capabilities. When firing its inaccurate rockets on A, B knows that some rockets will hit military targets and some will hit A’s civilians and thus trigger harsh retaliation by A. The risk of hitting A’s civilians could thus deter B from attacking A. B could invest in more accurate offensive systems that would effectively target A’s military infrastructure, without harming A’s civilians. But such investment is costly. A’s investment in defenses serves as a substitute for B’s investment in more accurate offensive systems. Knowing that A’s defenses will prevent serious harm to A’s civilians, B feels more free to fire its inaccurate rockets. A’s investment in defenses creates a positive externality—it helps B. And if it also helps B’s civilians, then such investment in defenses should be encouraged by international law.
D. Investment in Offensive Capabilities
This Article focuses on investments in defensive systems, but the analysis has some interesting parallels to investments in offensive capabilities. Assume that, at T0, Party A can choose between two investments. The first is an investment in a defensive system that would intercept 100 out of the 200 projectiles that Party B is expected to launch against A at T1. This is precisely the type of investment in defenses that we have been focusing on. The second option is to invest in an offensive system that would destroy 100 out of the 200 projectiles that B has before they are even launched and without causing any civilian casualties. It should be clear that the analysis of such an offensive investment closely parallels our analysis of investment in defenses.
In particular, the implications for international law are similar. Consider the positive-externality case and assume that A’s T0 offensive action—destroying 100 of B’s projectiles—helps B’s civilians, because now B’s T1 attack will inflict less harm on A and so A will respond with a less intense retaliatory attack at T2. International law should encourage A’s investment in such offensive technology. And this can be more effectively achieved by adopting our proposed interpretation of proportionality doctrine, namely, by using as the benchmark for the proportionality calculus B’s pre-investment, 200-projectile threat and not the actual harm that A incurred from B’s remaining 100 projectiles.
While the analysis can be analogously applied to investments in offensive capabilities, the analogy is not perfect. Specifically, the analogy works well if we assume, as we did in the preceding example, that A’s T0 offensive does not harm B’s civilians. But offensive systems are unlikely to be so precise. To take the opposite case: if A’s T0 offensive is as harmful to B’s civilians as A’s T2 retaliatory attack, then there is no reason to encourage A’s investment in such offensive capabilities. Indeed, one of the key differences between defensive and offensive systems is that the former causes no collateral damage.
E. Probabilistic Harm
Our basic analysis, while elucidating some challenges in the interpretation of proportionality doctrine, also glossed over certain other challenges. One such challenge involves the treatment of probabilistic harm. The basic problem exists even in a world without defenses, so we begin by considering a no-defenses scenario. Assume that at T1 Party B launches a single missile against A. This missile has a 50% chance of hitting a major city and killing ten civilians and a 50% chance of falling in international waters and causing no harm. If the missile hits A, then it seems that the proportionality doctrine would permit A to retaliate and inflict on B a harm that is proportional to the ten casualties (we bracket out the question of whether and how much proportionality permits an additional measure of force for future deterrence). What if the missile falls in the water? Is A permitted to inflict harm that is proportional to the ten potential casualties, to the expected harm of five casualties, or to the actual harm which is zero? According to our understanding, the proportionality doctrine would apply a baseline that is somewhere between ten and five casualties.
Now add defenses. Party B still fires one missile, but now assume that, without defenses, this missile will cause ten casualties for sure. At T0 Party A invests in a defensive system that can intercept an incoming missile with a 50% probability. If the missile is not intercepted and hits A, then it seems that the proportionality doctrine would permit A to retaliate and inflict on B a harm that is proportional to the ten casualties. What if the missile is intercepted? Is A permitted to inflict harm that is proportional to the ten potential casualties, to the expected harm of five casualties, or to the actual harm which is zero? As before, according to our understanding, the proportionality doctrine would apply a baseline that is somewhere between ten and five casualties. This indeterminacy afflicts the standard interpretation of proportionality. It does not affect the extreme version of our alternative interpretation that uses the “without defenses” benchmark for the proportionality analysis. Of course, we do not support this extreme version; we argue that the effect of defenses should be discounted but not entirely ignored. It is impossible to put a number on the appropriate level of the discount—definitely not a single number that would apply to all conflicts. And this introduces a different type of indeterminacy.
F. Agency Problem on A’s Side
We have thus far focused on the agency problem that might afflict Party B—the concern that B’s political or military leadership will not fully account for the cost that the conflict imposes on B’s civilian population. Of course, agency problems are not limited to any one party. Party A might also suffer from an agency problem, such that A’s political or military leadership might not be a faithful agent of A’s civilian population. One major concern is that A’s leadership might seek an excuse to attack B and thus avoid investment in defenses that could take away such an excuse. This dynamic would be especially problematic in the positive-externality case, where A’s defenses help not only A’s civilians but also B’s.
G. Commitment Problem
There is another reason for investing in defenses: A may have a commitment problem. Ex ante A does not want to retaliate forcefully against B, especially when the retaliation is costly to A—both in human lives and in economic resources. But A realizes that, if B’s attack harms A’s civilians, A would be pressured to retaliate forcefully. Specifically, public outcry following an attack by B that inflicted civilian casualties on A might pressure A’s political or military leadership to retaliate forcefully against B. In this context, A may invest in defenses as a commitment mechanism; defenses reduce the probability that B’s attack will harm A’s civilians and thus reduce the probability that A would be pressured to retaliate forcefully.
H. Long-Term Effects
Defenses might have additional long-term implications. Specifically, by reducing the pain from hostilities, defenses might work to prolong the conflict overall. In principle, this type of concern is not fundamentally different from a general concern that IHL—with its goal of mitigating the harm of war—might make war more bearable and, therefore, possibly longer and ultimately worse in its humanitarian effects. We are therefore hesitant to make too much of it.
Still, this long-term cost can be incorporated into our analysis as another type of externality. So far we assumed that the defending party decides how much to invest in defenses and fully internalizes all the effects of these investments on the defender. Now deconstruct the defender. The investment decision is made by the current leadership of the defending state, but this leadership—for political or other reasons—is shortsighted and places insufficient weight on long-term consequences. In particular, the leadership does not account for the effects of defenses on the duration of the conflict. If more effective defenses reduce the prospect of resolving the conflict, the intertemporal externality would inefficiently increase investment in defenses.
I. Application: Iron Dome
The Israel–Hamas conflict provides an important context for testing our theory. We now offer some suggestive evidence on the Iron Dome defense system and its effects on the conflict between Israel and Hamas, and link it back to our theoretical analysis. This discussion relies on the data collected by Richemond-Barak and Feinberg on Iron Dome and its effects,[116] as well as on a RAND Corporation study of the Israeli wars in Gaza and the role of Iron Dome within them,[117] and it will be quite tentative, given the limitations of the available data.
First, we note that Iron Dome satisfied our basic assumption about defense systems—it reduced the harm incurred by the defending party, Israel. Indeed, the evidence shows that Iron Dome was very effective in intercepting Hamas rockets. Richemond-Barak and Feinberg report a success rate of about 90%.[118] There is also evidence supporting our prediction that less harm—namely fewer casualties—leads to less intense retaliation. According to Richemond-Barak and Feinberg, the efficacy of Iron Dome allowed Israel to opt for a limited response in the form of targeted airstrikes.[119] Evidence also suggests that Hamas substantially intensified its rocket attacks after Iron Dome became operational, increasing the daily average of projectiles threefold (or more).[120] Our basic analysis suggested that better defenses are expected to reduce the intensity of Hamas’s attacks. Yet, the extensions that we discussed offer an explanation. Consider the marginal-cost-of-defenses extension. Hamas may have sought to inflict nonlethal, yet significant costs on Israel—by forcing it to launch the expensive Iron Dome interceptor missiles. Or consider the imperfect-rationality extension. Hamas may have been satisficing—firing rockets until it inflicts a minimal level of harm on Israel. Also, Hamas may have fired more rockets in a failed attempt to overwhelm the Iron Dome system.
In addition, investment in defense systems may lead to a cat-and-mouse game where the attacking party—in response to an existing defense system—develops new modes of attack; the defending party develops a new defense system; the attacking party again revamps its attack mode; etc. Indeed, Hamas’s efforts to build infiltration tunnels may well be a response to Iron Dome’s success in intercepting Hamas’s rockets.[121]
An additional relevant fact is that, according to some accounts, the reason Operation Protective Edge lasted for as long as fifty days (longer than previous conflicts with Hamas) is that Israel was able to take its time pursuing operational goals as its civilians were largely shielded from ongoing Hamas attacks. The RAND report cited an Israeli think-tank analyst who claimed that Israeli Defense Minister Bogie Ya’alon could afford “to change the concept of operations to attrition rather than a decisive campaign. . . . There are no casualties, no harm to Israel, so no need to stop the campaign.”[122] This account is consistent with our Scenario 2 analysis, and could mean that defenses have allowed the conflict to continue at the cost of greater threat to civilians. On the other hand, Hamas reportedly rejected several proposed ceasefires before the end of the cycle of clashes, suggesting that Iron Dome is not the only reason for the longer round of clashes.
Beyond any particular cycle of hostilities, it is possible that Iron Dome, precisely because of its effectiveness, has contributed to the endurance of the conflict between Israel and Hamas. Indeed, some commentators have described Iron Dome as a dangerous “tactical miracle,” which, by making armed clashes with Hamas more bearable for Israelis, also threatened to numb Israeli society against the dangers of allowing the conflict to simmer without a comprehensive political resolution.[123] The Economist, for instance, claimed that “[s]ome wonder if Iron Dome’s main problem is in fact a political one. The system’s success means that Binyamin Netanyahu, the Israeli prime minister, has been able to use Iron Dome to maintain his policy of conflict management, with less fear of retaliation.”[124] This is a perfectly plausible and serious concern. We are also mindful of the fact that there are many contributors to the endurance of the conflict, and it would be difficult—if not impossible—to isolate and weigh the specific contribution of Iron Dome.[125]
From a legal-policy perspective, perhaps the most important question is whether Israel’s investment in Iron Dome protected only Israelis or also saved lives on the Palestinian side. As noted above, it appears that Iron Dome allowed Israel, at least according to some analysts, to settle for less intense retaliatory attacks. And there is some evidence of a reduction in casualties on the Palestinian side in comparison with earlier large-scale clashes between the parties.[126] Also, the RAND study suggested that Iron Dome limited the need to rely on a ground operation in Gaza, and that “[a]s a result (and somewhat counterintuitively), Iron Dome likely saved Palestinian civilian lives—as well as Israeli ones.”[127] But the evidence is inconclusive.
Ultimately, if Iron Dome did reduce the number of Palestinian casualties, then Israel’s investment in this defensive system created a positive externality. This means that Israel should be encouraged to invest more in Iron Dome (and related systems) and that the proportionality principle should not be interpreted in a way that would deter such investment.
In this last context, it should be noted that, at least according to the RAND researchers, Israeli decision makers were cognizant of the political—if not legal—constraints that Iron Dome imposed in terms of its effects on proportionality calculations: according to their report,
[m]any IDF officers and policymakers, in fact, view Iron Dome as both a blessing and a curse. The system—in their opinion—obviously saves lives, but it also complicates Israel’s ability to justify the operation to an international audience. As one senior Israel policymaker argued, Iron Dome “is a blessing because it buys Israel time, but Israel needs an excuse for why they are killing Palestinians in operations. They need this to convince the Americans. When Iron Dome works so well and so few Israelis die, Israel loses the justification for the operation.”[128]
One RAND researcher later added, “[I]nternational reports like the UN Independent Commission of Inquiry on the 2014 Gaza Conflict show the international political cost Israel paid for the perception of disproportionate aggression.”[129]
V. A Consequentialist Theory of Defenses: Symmetric Defenses
This Part focuses on symmetric defenses, where both parties have at least the capacity to invest in defenses, even if they choose not to do so. It derives the privately optimal investment in defensive measures (in the absence of legal rules) and compares it to the socially optimal level.
In the symmetric-defenses case, we emphasize the coordination problem. There are two possible equilibria: one where both parties invest substantial amounts of resources in defenses and rely on these defenses to safeguard their civilian population, and another where both parties invest minimally in defenses and rely on deterrence—the threat of forceful retaliation against an adversary with minimal defenses—to achieve a similar level of safety. (We assume that such an equilibrium exists even taking account of limits imposed by the proportionality principle.) In this minimal-defenses equilibrium, the parties can use the resources that would otherwise be devoted to defenses for other purposes—healthcare, education, etc. While both parties would prefer minimal investment in defenses, they might end up with excessive investments. We suggest that the 1972 U.S.–U.S.S.R. Anti-Ballistic Missile (ABM) Treaty solved this coordination problem.[130] We also suggest that the recent skirmishes between North Korea and its neighbors, in which only one side (the United States, Japan) employed defensive measures,[131] can be better understood using our analytical framework.
The analysis from the asymmetric-defenses case carries over, in large part, to the symmetric-defenses case. There is one important difference, however. In the symmetric-defenses case, A’s decision to invest in defenses depends on B’s decision to invest in defenses, and vice versa. Better defenses produce a tactical or even strategic advantage in a conflict situation. The other party is bound to respond. Initially, we assume that this response is only defensive—B responds to A’s increased investment in defenses by increasing its own investment. Later, we will consider the possibility of an offensive response—B might respond to A’s increased investment in defenses by increasing its investment in offensive capabilities.
Focusing on defensive responses, we begin by defining the parties’ reaction functions. Let and denote A’s investment in defense and B’s investment in defense, respectively. We have seen that A’s investment is a function of B’s investment. We can thus write: , where is A’s reaction function. We know that is an increasing function, namely, it translates a higher investment by B, i.e., a higher , into a higher investment by A, i.e., a higher . Similarly, B’s investment is a function of A’s investment. We can thus write: , where is B’s reaction function. We know that is an increasing function, namely, it translates a higher investment by A, i.e., a higher , into a higher investment by B, i.e., a higher . The key question, as we will shortly see, is whether these increasing reaction functions increase at an increasing rate or rather at a decreasing rate.[132]
A. High-Investment Equilibrium
We first consider the case where the reaction functions are increasing at a decreasing rate. This case is depicted in Figure 1a. The functions intersect in two separate points, representing two sets of equilibrium defense levels: (1) the equilibrium, where both parties invest zero in defenses, and (2) the equilibrium, where both parties invest a positive, and possibly very large, amount in defenses. We will show that only the equilibrium is stable and thus reflects the outcome in the symmetric-defenses case when the reaction functions are increasing at a decreasing rate.
Figure 1a: Reaction Functions Increase at a Decreasing Rate
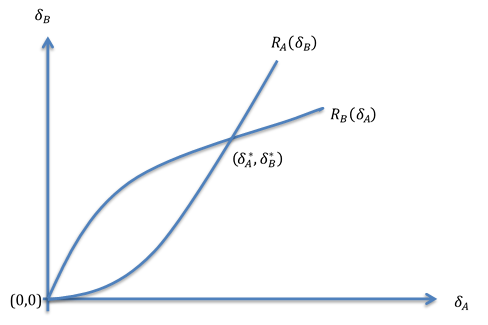
We first show that the equilibrium is unstable. Assume that we are at the equilibrium, namely, that both parties invest zero in defenses. Now assume that one party, Party A for example, slightly increases its investment in defenses. Party B will respond by also increasing its defenses. Party A will then increase its defenses even further. And so on until we converge on the equilibrium. This dynamic is depicted in Figure 1b.
Figure 1b: Instability of the (0,0) Equilibrium
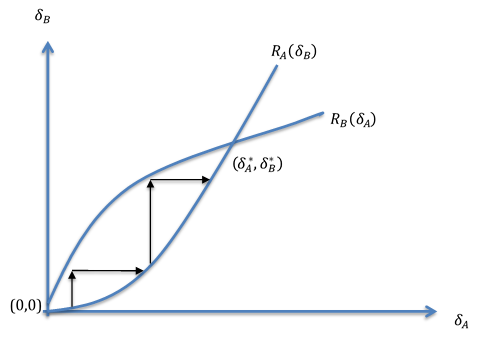
We next show that the equilibrium is stable. Assume that we are at the equilibrium and that Party A slightly decreases its investment in defenses. Party B will respond by also decreasing its investment in defenses, but only slightly, since B’s reaction curve has a mild slope near the equilibrium. A will then respond by increasing its investment in defense. Then B will also increase its investment, until we return to the equilibrium. (Similarly, if we start at the equilibrium and Party A slightly increases its investment in defenses, we will also converge back to the equilibrium.)
We have seen that the equilibrium is the only stable equilibrium in the symmetric-defenses case. In this equilibrium both parties invest, possibly large amounts, in defense. The preceding analysis reveals a coordination problem akin to the Prisoners’ Dilemma. Party A increases its defenses because Party B invests in defenses. And Party B increases its defenses because Party A invests in defenses. If they could coordinate, the parties may prefer that both invest minimally in defenses.[133] From an overall social or humanitarian perspective, the parties’ large investments in defenses are clearly undesirable in the negative-externalities case (see Part III above). In the positive-externalities case, the equilibrium investment levels, which are privately excessive, may be socially desirable; however, they might also be excessive from an overall social or humanitarian perspective. There is no reason why the equilibrium investment levels, which are the product of a collective-action problem, would exactly coincide with the socially optimal levels.
B. Low-Investment Equilibrium
We now consider the case where the reaction functions are increasing at an increasing rate. This case is depicted in Figure 2. (Figure 2 is similar to Figure 1a, only that the graph representing Party A’s reaction function now represents Party B’s reaction function, and vice versa.) As before, the functions intersect in two separate points, representing two sets of equilibrium defense levels: (1) the equilibrium, where both parties invest zero in defenses, and (2) the equilibrium, where both parties invest a positive, and possibly very large, amount in defenses. But now only the equilibrium is stable. (This can be shown using the dynamic reasoning from subpart V(A).) The low-investment equilibrium may be socially optimal in the negative-externalities case, but not in the positive-externalities case.
Figure 2: Reaction Functions Increase at an Increasing Rate

C. An Offensive Response
We have thus far focused on defensive responses—namely, Party B responds to Party A’s increased investment in defenses by increasing its own investment in defenses. But there could also be an offensive response. If Party A invests in better defenses, Party B may invest in improving its offensive capabilities so that it could overcome A’s enhanced defenses.[134] From Party B’s perspective, offensive and defensive investments are substitutes in terms of their effect on the overall conflict between the two parties. Therefore, the preceding analysis can readily be extended to include offensive investments. As before, we have a low-investment equilibrium and a high-investment equilibrium, albeit now the investment can be an offensive investment. From a normative perspective, the shift to offensive investments places us squarely in the negative-externalities case; a party’s investment in offensive capabilities will harm, not help, the other party’s civilian population. Accordingly, the equilibrium is socially desirable, and we should be concerned when the parties’ reaction functions are increasing at a decreasing rate, rendering this equilibrium unstable.
D. Application: The 1972 ABM Treaty
This analysis sheds light on strategic interaction between the United States and the Soviet Union with respect to missile defense systems against the mutual ICBM threat. Employing our framework, assume that both countries have large nuclear arsenals and must now decide how much to invest in defenses. From a social perspective, the goal is to minimize the probability of nuclear destruction, while also minimizing resource expenditures. There seem to be two scenarios where the probability of nuclear destruction is small:
- Scenario 1: The United States and the Soviet Union invest substantial resources in creating missile defense systems that would protect, albeit imperfectly, against a nuclear attack. This scenario corresponds to the equilibrium.
- Scenario 2: The United States and the Soviet Union do not invest any resources on missile defense. The unbearable cost of nuclear war serves as an effective deterrent. This scenario corresponds to the equilibrium.
Here, Scenario 2 is socially preferable. We are likely in the negative-externalities case. Moreover, Scenario 2 is as good as or better than Scenario 1 in terms of the risk of a nuclear disaster. And it frees up substantial resources—resources that under Scenario 1 would be invested in developing a missile defense system—and allows the government to invest these resources in health, education, etc. In other words, minimal defenses are optimal. Yet, in the absence of a coordination mechanism, an arms race or, more accurately, a defense-systems race would result in excessive investment by both parties in antimissile systems. Within our framework, the reaction functions are increasing at a decreasing rate and so the equilibrium, which represents Scenario 1, is the stable equilibrium. The 1972 ABM Treaty provided the coordination mechanism that avoided this bad, excessive-investment outcome.
In the asymmetric-defenses case, we also considered the long-term effects of defenses. What are the long-term effects of defenses in this, symmetric-defenses context? Would they increase or decrease the duration of the conflict? The ABM Treaty, by limiting the effective defenses that both the United States and the Soviet Union were able to deploy, perpetuated the Mutually Assured Destruction balance of the Cold War.[135] It is not clear, however, whether more effective defenses on both sides—a likely result without the ABM Treaty—would have resulted in a longer or shorter conflict. Recall that some observers were concerned that the SDI initiative would break the balance of power and dangerously raise tensions between the two superpowers. At the same time, at least some commentators believe that the asymmetric defensive capacity of the SDI, however theoretical, proved instrumental in the long run in convincing the Soviets to negotiate with the United States and, ultimately, to end the Cold War.[136] Given that the Soviet Union would have been unable to meet the costs of a comparable defensive program, in our framework, the SDI can be understood as shifting the conflict from the symmetric-defenses case to the asymmetric-defenses case.
E. Application: North Korea
Our analysis of the symmetric-defenses case can also shed light on the recent escalation of military tensions between North Korea and its neighbors. In these conflicts, one side, North Korea, is clearly focusing on offensive capabilities, while the other, the United States, Japan, and—potentially—South Korea (with the aid of the United States), is employing sophisticated antimissile defenses (in addition to its existing, formidable offensive capabilities).[137] As our analysis predicts, increased investment by one party triggers increased investment by the other. A party’s choice between defensive and offensive investments depends, among other things, on the marginal product of each type of investment. In the case of North Korea, it seems like the country’s political and military leadership has chosen the offensive path. Given their existing offensive infrastructure, namely, the North’s nuclear missile program, and the lack of a substantial defensive infrastructure, the marginal product of additional offensive investments is greater for North Korea. On the other side, the emphasis is on defensive measures. This defensive focus can be explained by the greater concern for the protection of civilians or simply by the fact that, with the help of the United States, North Korea’s adversaries already have formidable offensive capabilities. From a normative perspective, as we have seen, the arms race is particularly troubling when one party chooses to invest in offensive capabilities. That is why the world is more concerned about North Korea’s offensive investments and less about the defensive investments by South Korea and Japan. (There are, of course, additional reasons why the international community is focusing on North Korea.)
Conclusion
Defenses are of paramount importance on both descriptive and normative levels. Countries invest billions of dollars in developing and deploying defensive systems. And these systems affect the number of casualties—both on the side of the defending party and on the side of the attacking party. This Article developed a comprehensive analytical framework for the assessment of defenses. This framework can help policymakers and scholars understand the overall effects of investment in defenses. It can also inform international law as it grapples with how to incorporate defenses into the proportionality calculus.
Our analysis emphasizes the strategic relationship between offensive and defensive actions and investments. In some cases, defense and offense are strategic substitutes. Defenses allow the defender to exercise more restraint on the offensive front. In such cases, defenses may create a positive externality on the nondefending party. International law should thus be careful not to deter investment in defenses. We have shown that proportionality doctrine, as commonly understood, might deter socially desirable investment in defenses and suggested a new understanding of proportionality that avoids these unintended consequences.
In other cases, defense and offense are strategic complements. Defenses, by protecting the defending party from possible retaliation, allow this party to engage in more intense offensive action. In such cases, defenses likely impose a negative externality on the nondefending party, and we should be less concerned if international law, through the proportionality doctrine, discourages investment in defenses.
- .See generally Ron E. Hassner & Jason Wittenberg, Barriers to Entry: Who Builds Fortified Boundaries and Why?, Int’l Security, Summer 2015, at 157 (exploring the modern trend of fortified boundaries). ↑
- .Only three of those—the United States, Russia, and Israel—have the capability to intercept intercontinental ballistic missiles; the others have a tactical capacity to intercept missiles of lower velocity. See Ground-Based Midcourse Defense (GMD) System, Ctr. for Strategic & Int’l Studies (June 14, 2018), https://missilethreat.csis.org/system/gmd/ [https://perma.cc/9J6P-Y5BE] (describing the United States’ GMD system); Jana Hankova, Current Developments in Russia’s Ballistic Missile Defense, George C. Marshall Inst. 3–4 (Apr. 2013) (describing Russian missile defense systems); Arrow 3 (Israel), Ctr. for Strategic and Int’l Studies (Aug. 11, 2016) [hereinafter CSIS, Arrow 3 (Israel)], https://missilethreat.csis.org/defsys/arrow-3/ [https://perma.cc/LG63-6FHH] (describing the Israeli Arrow 3 defense system). ↑
- .Gerry Doyle, If Missiles Are Headed to Guam, Here Is What Could Stop Them, N.Y. Times (Aug. 11, 2017), https://www.nytimes.com/2017/08/11/world/asia/guam-north-korea-missile-defense.html [https://perma.cc/T4Z5-H6UP]; Teppei Kasai & Tim Kelly, Japan Missile Defense Drill Aims to Ease Concern Over North Korean Threat, Reuters (June 21, 2017), https://www.reuters.com/article/us-northkorea-missiles-japan/japan-missile-defense-drill-aims-to-ease-concern-over-north-korean-threat-idUSKBN19C0JM [https://perma.cc/9V4N-644F]; Motoko Rich, North Korea Fires More Missiles as Seoul Puts Off U.S. Defense System, N.Y. Times (June 7, 2017), https://www.nytimes.com/2017/06/07/world/asia/south-korea-thaad-missiledefense
-us.html [https://perma.cc/BP68-HLX2]. ↑
- .See Iron Dome (Israel), Ctr. for Strategic & Int’l Studies (Apr. 14, 2016) [hereinafter CSIS, Iron Dome (Israel)], https://missilethreat.csis.org/defsys/iron-dome/ [https://perma.cc/AB22-D69U] (describing the Israeli Iron Dome defense system); Terminal High Altitude Area Defense (THAAD), Ctr. for Strategic & Int’l Studies (June 14, 2018), https://missilethreat.csis.org
/system/thaad/ [https://perma.cc/Z5WH-JKCC] (describing the United States’ THAAD system and foreign sales of the system). The United States was planning on deploying such systems in South Korea, a plan that was rejected by the new South Korean leader. Rich, supra note 3. ↑
- .The distinction between deterrence by denial and deterrence by threat of punishment is usually attributed to Glenn H. Snyder. In Snyder’s authoritative definition, deterrence by denial is achieved by “the capability to deny the other party any gains from the move which is to be deterred.” Glenn H. Snyder, Deterrence and Power, 4 J. Conflict Resol. 163, 163 (1960); see also Glenn H. Snyder, Deterrence and Defense: Toward a Theory of National Security 12 (1961) [hereinafter Snyder, Deterrence and Defense] (discussing deterrence strategy); Glenn H. Snyder, Deterrence by Denial and Punishment 3 (1959) [hereinafter Snyder, Deterrence by Denial and Punishment] (distinguishing punishment deterrence and denial deterrence). ↑
- .We use the term “defender” here not in any normative sense but only to denote the party that employs the defensive system. ↑
- .See, e.g., Rich, supra note (explaining that South Korea’s leader suspended the deployment of American missile defense systems in response to political pressures). ↑
- .Other scholars have documented and reported the proliferation of lawyers in western armed forces and the rise in importance of legal considerations in planning and executing military operations. See, e.g., Laura A. Dickinson, Military Lawyers on the Battlefield: An Empirical Account of International Law Compliance, 104 Am. J. Int’l L. 1, 10 (2010) (discussing the role of U.S. military lawyers in operational decision-making post-Vietnam War); Michael P. Scharf, International Law in Crisis: A Qualitative Empirical Contribution to the Compliance Debate, 31 Cardozo L. Rev. 45, 46–47 (2009) (examining how international law influences American foreign policy). ↑
- .See, e.g., Michael Nacht, The Politics: How Did We Get Here? (discussing the Anti-Ballistic Missile Treaty), in Contemporary Nuclear Debates: Missile Defenses, Arms Control, and Arms Races in the Twenty-First Century 3, 4–5 (Alexander T.J. Lennon ed., 2002) [hereinafter Contemporary Nuclear Debates]; Michael N. Schmitt & John J. Merriam, The Tyranny of Context: Israeli Targeting Practices in Legal Perspective, 37 U. Pa. J. Int’l L. 53, 65–66 (2015) (discussing the Iron Dome system). ↑
- .The working paper version of this Article contains a mathematical Appendix that supports and generalizes the qualitative analysis in the text. Oren Bar-Gill & Gabriella Blum, Defenses (Harv. Pub. Law Working Paper No. 18-12, 2018), https://papers.ssrn.com/sol3/papers.cfm?
abstract_id=3123133 [https://perma.cc/89GJ-BXCH]. ↑
- .The notion of “deterrence by denial” was first elaborated by Snyder. See Snyder, Deterrence by Denial and Punishment, supra note 5, at 3 (introducing the concepts of punishment deterrence and denial deterrence); see also Snyder, Deterrence and Defense, supra note 5, at 14–15 (expanding on these concepts). The “deterrence by denial” theory was further developed in, for example, Paul K. Davis & Brian Michael Jenkins, Deterrence and Influence in Counterterrorism: A Component in the War on al Qaeda xii, 15 (2002) and C. Poppe et al., “Whither Deterrence?” Final Report of the 2001 Futures Project 4, 13 (2002); see also Lawrence Freedman, Deterrence 36–40 (2004) (contrasting deterrence by denial and deterrence by punishment); Paul K. Davis, Toward Theory for Dissuasion (or Deterrence) by Denial: Using Simple Cognitive Models of the Adversary to Inform Strategy 2 (RAND Corp. Working Paper No. 1027, 2014), https://www.rand.org/pubs/working_papers
/WR1027.html [https://perma.cc/ETZ6-EDM9] (discussing the strategy of “deterring an action by having the adversary see a credible capability to prevent him from achieving potential gains adequate to motivate the action”). For a recent survey, see Jeffrey W. Knopf, The Fourth Wave in Deterrence Research, 31 Contemp. Security Pol’y 1, 12–14 (2010). Deterrence by denial encompasses “active defenses,” which are the focus of this Article, but also “passive defenses” (or “civil defenses”) and general resilience strategies designed to deny the aggressor’s goal of terrorizing or demoralizing the defending party. See, e.g., Freedman, supra, at 37 (differentiating between passive and active defenses); Knopf, supra, at 6, 13 (discussing active defenses and resilience strategies against terrorism). ↑
- .For a discussion of the different types of defenses, see, for example, Freedman, supra note 11, at 37; Snyder, Deterrence and Defense, supra note 5, at 14–15; and Knopf, supra note 11, at 13. ↑
- .See, e.g., Bernard Brodie, Strategy in the Missile Age 202 (1959) (arguing that “the history of the race [between offense and defense] thus far suggests that there is always a hole, an Achilles’ heel”). ↑
- .See, e.g., Snyder, Deterrence and Defense, supra note 5, at 275 (making similar assumptions). ↑
- .CSIS, Iron Dome (Israel), supra note . ↑
- .Daphné Richemond-Barak & Ayal Feinberg, The Irony of the Iron Dome: Intelligent Defense Systems, Law, and Security, 7 Harv. Nat’l Security J. 469, 473 (2016). ↑
- .Id. ↑
- .Id. ↑
- .Id. ↑
- .Id. at 473 n.6; see also Arnon Gutfeld, From ‘Star Wars’ to ‘Iron Dome’: US Support of Israel’s Missile Defense Systems, 53 Middle Eastern Stud. 934, 944 (2017) (summarizing “the success of the Iron Dome in shooting down large amounts of projectiles launched at Israel during Operation Protective Edge”). ↑
- .Dan Williams, Israel’s Barak Seeks Three More Iron Dome Rocket Interceptors, Reuters (Nov. 16, 2012), https://www.reuters.com/article/us-palestinians-israel-arms-irondome/israels-barak-seeks-three-more-iron-dome-rocket-interceptors-idUSBRE8AF1AM20121116 [https://perma.cc/9AES-7HMK]. ↑
- .Judah Ari Gross, Israel to Deploy David’s Sling, Final Piece of Missile Defense Shield, Times Isr. (Mar. 20, 2017), https://www.timesofisrael.com/israel-to-deploy-davids-sling-in-april-completing-missile-defense-shield/ [https://perma.cc/4HJZ-BS9Q]. ↑
- .Id. ↑
- .Gutfeld, supra note , at 942–43 (describing a $1.25 billion investment by the United States). ↑
- .The high costs of the Tamir are driven by the autonomous sensory systems that guide it to its target after launch. ↑
- .The true costs of Grad depend on where they were purchased from and which model is used. See, e.g., Yossi Melman, Under Fire, Tablet (Mar. 15, 2012), http://www.tabletmag.com/jewish-news-and-politics/94134/under-fire [https://perma.cc/2RUP-Z2BP] (“One Grad rocket costs roughly $1,000.”). ↑
- .CSIS, Iron Dome (Israel), supra note 4. ↑
- .Jean-Loup Samaan, Another Brick in the Wall: The Israeli Experience in Missile Defense 33–34 (2015), http://www.dtic.mil/cgibin/GetTRDoc?Location=U2&doc
=GetTRDoc.pdf&AD=ADA615822 [https://perma.cc/HP62-R9P8] (considering whether “the ratio between the cost of an Iron Dome battery and a Qassam rocket is such that it does not dissuade Palestinian organizations”). ↑
- .We acknowledge that in “cost discrepancy” it is not enough to consider the absolute costs of each incoming rocket or intercepting missile, but also the parties’ respective abilities to bear these costs on a recurring basis. ↑
- .Richemond-Barak & Feinberg, supra note 16, at 484–85. ↑
- .Christa Case Bryant, Hamas Attacks by Tunnel Rattle Israelis on Gaza Border, Christian Sci. Monitor (July 28, 2014), https://www.csmonitor.com/World/Middle-East/2014/0728/Hamas
-attacks-by-tunnel-rattle-Israelis-on-Gaza-border [https://perma.cc/B2SX-5K3X]; Aaron J. Klein & Mitch Ginsburg, Could Israeli Soldiers, Not Civilians, Be the Target of the Attack Tunnels?, Times Isr. (July 29, 2014), http://www.timesofisrael.com/soldiers-not-civilians-are-tunnel-infiltration-goals-says-senior-intelligence-source/ [https://perma.cc/ZX2J-YTCX]; Heather Saul, Israeli Soldier ‘Captured in Tunnel Attack’ by Gaza Militants, Independent (Aug. 1, 2014), https://www.independent.co.uk/news/world/middle-east/israeli-soldier-feared-captured-in-tunnel-attack-by-militants-9642469.html [https://perma.cc/H5LA-P2XU]. ↑
- .Ido Ben-Porat, Minister Bennett: ‘Destruction of Tunnels Prevented Mass-Casualty Attack,’ Arutz Sheva (Feb. 28, 2017), http://www.israelnationalnews.com/News/News.aspx
/225860 [https://perma.cc/UL9Y-ETDM]; Klein & Ginsburg, supra note 31. ↑
- .Stanford Arms Control Grp., International Arms Control: Issues and Agreements 217 (Coit D. Blacker & Gloria Duffy eds., 2d ed. 1984) (“The dramatic proliferation of warheads allowed by MIRV ensured that even an extensive ABM effort could not limit the destructiveness of an American retaliatory strike.”). ↑
- .Nick Paton Walsh, Moscow Extends Life of 144 Cold War Ballistic Missiles, Guardian (Aug. 19, 2002), https://www.theguardian.com/world/2002/aug/20/russia.nickpatonwalsh [https://perma.cc/GA5J-QTFX]. ↑
- .Nacht, supra note , at 4–5. ↑
- .Treaty on the Limitation of Anti-Ballistic Missile Systems, U.S.–U.S.S.R., May 26, 1972, 23 U.S.T. 3435 [hereinafter 1972 ABM Treaty]. ↑
- .Id. at 3440. ↑
- .Richard L. Garwin, A Defense that Will Not Defend, in Contemporary Nuclear Debates, supra note 9, at 29, 41. ↑
- .John W. Finney, Safeguard ABM System to Shut Down; $5 Billion Spent in 6 Years Since Debate, N.Y. Times (Nov. 25, 1975), https://www.nytimes.com/1975/11/25/archives/safeguard-abm-system-to-shut-down-5-billion-spent-in-6-years-since.html [https://perma.cc/7W2T-KQVW]. ↑
- .Nacht, supra note 9, at 5–6. ↑
- .Id. ↑
- .See National Missile Defense Act of 1999, Pub. L. No. 106-38, § 2, 113 Stat. 205 (“It is the policy of the United States to deploy as soon as is technologically possible an effective National Missile Defense system capable of defending the territory of the United States against limited ballistic missile attack . . . .”); Greg Thielmann, Rumsfeld Reprise? The Missile Report That Foretold the Iraq Intelligence Controversy, Arms Control Ass’n (July 1, 2003), https://www.armscontrol.org/act/2003_07-08/thielmann_julaug03 [https://perma.cc/XU5F-46SR] (explaining Iran and North Korea’s influence). ↑
- .Bonnie Berkowitz & Aaron Steckelberg, If North Korea Fires a Nuclear Missile at the U.S., How Could It Be Stopped?, Wash. Post (Nov. 29, 2017), https://www.washingtonpost.com
/graphics/2017/world/north-korea-missile-defense/ [https://perma.cc/S6NH-GUDA]. ↑
- .See, e.g., CSIS, Arrow 3 (Israel), supra note 2 (Israel); India Plans to Use Laser Weapons in Ballistic Missile Defence, DNA India (Jan. 18, 2009), https://www.dnaindia.com/world/report-india-plans-to-use-laser-weapons-in-ballistic-missile-defence-1222517 [https://perma.cc/9TWR-Q5JZ] (India); Japan Plans Tokyo Missile Shield, BBC (Jan. 15, 2008), http://news.bbc.co.uk/2/hi
/asia-pacific/7188698.stm [https://perma.cc/UB5J-CWX7] (Japan); Sol-Air Moyenne Portée/Terrestre (SAMP/T), Ctr. for Strategic & Int’l Studies (June 15, 2016), https://missilethreat.csis.org/defsys/samp-t/ [https://perma.cc/FM72-D3QQ] (France and Italy). ↑
- .Doyle, supra note 3; Kasai & Kelly, supra note 3; Rich, supra note 3. ↑
- .Thomas Karako, Missile Defense and the Nuclear Posture Review, Strategic Stud. Q., Fall 2017, at 48, 49. ↑
- .U.N. Charter art. 51; G.A. Res. 2625 (XXV), at 122–23 (Oct. 24, 1970). ↑
- .See Hans Kelsen, The Law of the United Nations 803 (1950) (“[T]he right of self-defence is conferred upon the states by a rule of general international law which has the character of jus cogens and consequently cannot be altered by treaty provisions.”). ↑
- .See, e.g., Emer de Vattel, The Law of Nations: Or, Principles of the Law of Nature, Applied to the Conduct and Affairs of Nations and Sovereigns 288 (Béla Kapossy & Richard Whatmore eds., Liberty Fund, Inc. 2008) (1758) (“Every nation, as well as every man, has therefore a right to prevent other nations from obstructing her preservation, her perfection, and happiness,—that is, to preserve herself from all injuries[:] and this right is a perfect one, since it is given to satisfy a natural and indispensable obligation . . . .”); 2 Hugo Grotius, De Jure Belli ac Pacis Libri Tres 172 (James Brown Scott ed., Francis W. Kelsey trans., Oxford Univ. Press 1925) (1625) (“Th[e] right of self-defence . . . has its origin directly, and chiefly, in the fact that nature commits to each his own protection . . . .”); 1 Oppenheim’s International Law § 127 (Robert Jennings & Arthur Watts eds., 9th ed. 1992) (“The right of self-defence[:] No state is obliged by customary international law to remain passive when another state takes action inimical to its legally protected interests.”). ↑
- .Hobbes’s Leviathan, for instance, is designed to protect individuals from each other as well as from foreign foes. Thomas Hobbes, Leviathan 106–10 (Edwin Curley ed., Hackett Publ’g Co. 1994) (1651). ↑
- .In some cases, the obligation is read from within the national constitution. See, e.g., Edwin Meese III, Who Is Responsible for America’s Security? 1 (2011), https://www.heritage.org/
the-constitution/report/who-responsible-americas-security [https://perma.cc/TU7Y-AE6D] (arguing that in the American context “the Constitution’s Framers viewed the security of the nation to be the foremost responsibility of the federal government”). ↑
- .U.N. Charter art. 51. ↑
- .Id. ↑
- .U.N. Charter art. 2, ¶ 4. Other international instruments, such as the 1970 General Assembly’s declaration on Friendly Relations and its 1974 Definition of Aggression, reinforce the Charter’s efforts to minimize the use of force between states and expound the many ways in which a state may be in violation of Article 2(4). G.A. Res. 2625 (XXV), at 122 (Oct. 24, 1970); G.A. Res. 3314 (XXIX), at 143 (Dec. 14, 1974). The 1998 Rome Statute of the International Criminal Court went further in seeking to impose individual criminal responsibility for the crime of aggression, though this part of the Statute is not yet operational. Rome Statute of the International Criminal Court art. 5, July 17, 1998, 2187 U.N.T.S. 90. ↑
- .See Malcolm N. Shaw, International Law 817–18 (7th ed. 2014) (observing that the “weight of opinion” favors the interpretation prohibiting any use of force); Louis Henkin, The Use of Force: Law and U.S. Policy (“[G]overnments generally have insisted on the interpretations most restrictive of the use of force: the Charter outlaws war for any reason . . . .”), in Right v. Might: International Law and the Use of Force 37, 40 (2d ed. 1991). ↑
- .U.N. Charter arts. 39–51. ↑
- .Id. art. 51. ↑
- .For an elaboration on the different debates surrounding Article 51 and the regime that governs the use of force by states, see Mary Ellen O’Connell, Self-Defense, Oxford Bibliographies (Nov. 30, 2015), http://www.oxfordbibliographies.com/view/document/obo-9780199796953/obo-9780199796953-0028.xml [https://perma.cc/PX6N-VFAE]. ↑
- .Id. ↑
- .Military and Paramilitary Activities In and Against Nicaragua (Nicar. v. U.S.), Judgment, 1986 I.C.J. Rep. 14, ¶ 194 (June 27); see also Legality of the Use by a State of Nuclear Weapons in Armed Conflict, Advisory Opinion, 1996 I.C.J. 66, ¶ 22 (July 8) (declining to clarify the appropriateness of the use of nuclear weapons on jurisdictional grounds). ↑
- .Nicar. v. U.S., 1986 I.C.J. at ¶ 194. In Just War Theory, the necessity requirement was formulated as the condition of “last resort.” Jens David Ohlin & Larry May, Necessity in International Law 36–37 (2016). ↑
- .See generally David Kretzmer, The Inherent Right to Self-Defense and Proportionality in Jus Ad Bellum, 24 Eur. J. Int’l L. 235 (2013) (discussing various tests for proportionality, such as the “narrow proportionality” test in the jus ad bellum context); Matthew C. Waxman, Regulating Resort to Force: Form and Substance of the UN Charter Regime, 24 Eur. J. Int’l L. 151 (2013) (reimagining doctrinal forms of regulations for force and self-defense). ↑
- .E.g., Yoram Dinstein, War, Aggression and Self-Defence 251 (6th ed. 2017); Noam Lubell, Extraterritorial Use of Force Against Non-state Actors 81 (2010); Tom Ruys, ‘Armed Attack’ and Article 51 of the UN Charter: Evolutions in Customary Law and Practice 95 (2010); Michael N. Schmitt, Responding to Transnational Terrorism Under the Jus ad Bellum: A Normative Framework, in International Law and Armed Conflict: Exploring the Faultlines 157, 171 (Michael N. Schmitt & Jelena Pejic eds., 2007). ↑
- .See Olivier Corten, The Law Against War: The Prohibition on the Use of Force in Contemporary International Law 481 (Christopher Sutcliffe trans., 2010) (“In practice I know of no precedent where an act of self-defence has been condemned for the sole reason that its author failed to prove that it had not first exhausted all possible peaceful means.”); Dinstein, supra note 63, at 251 & n.1501 (describing a special exemption when no feasible peaceful options exist); Lubell, supra note 63, at 81 (noting that “all other alternative effective means” must be attempted before forcible measures but only “if they can put an end to the ongoing danger”); Ruys, supra note 63, at 97–98 (“[T]he ‘last resort’ condition has been of relatively little practical significance.”). ↑
- .Dinstein, supra note 63, at 251; Ruys, supra note 63, at 95. ↑
- .Ian Brownlie, International Law and the Use of Force by States 365–67 (1963). ↑
- .Note that disagreements also surround the question of what types of harms that are inflicted in the course of a military campaign should count in the proportionality calculation. For instance, all would agree that civilian casualties on the enemy side must be weighed against the security gains sought in the operation, but not all agree that enemy combatant casualties should count in the same way. ↑
- .Corten, supra note , at 488–93; Oscar Schachter, The Right of States to Use Armed Force, 82 Mich. L. Rev. 1620, 1637 (1984). ↑
- .Dinstein, supra note 63, at 287; see D.N. Kolesnik, The Development of the Right to Self-Defence (“Action in self-defense may be offensive militarily and may extend to the territory of the attacking side to the degree necessary to eliminate and prevent a renewal of armed attack.”), in The Non-Use of Force in International Law 153, 157 (W.E. Butler ed., 1989). ↑
- .Avra Constantinou, The Right of Self-Defence Under Customary International Law and Article 51 of the United Nations Charter 162, 170–71 (2000). ↑
- .Kretzmer, supra note 62, at 237 (citing Anthony Clark Arend & Robert J. Beck, International Law and the Use of Force: Beyond the UN Charter Paradigm 165–66 (1993); Albrecht Randelzhofer, Article 51, in 1 The Charter of the United Nations: A Commentary 788, 805 (Bruno Simma ed., 2d ed. 2002)). ↑
- .Corten, supra note 64, at 484–93; Christine Gray, International Law and the Use of Force 160 (3d ed. 2008); Rosalyn Higgins, Problems and Process: International Law and How We Use It 231–32 (1994). ↑
- .F.M. Kamm, Taking Just War Seriously in Gaza, Bos. Rev. (July 31, 2014), http://bostonreview.net/books-ideas/fm-kamm-taking-just-war-seriously-gaza [https://perma.cc/7DP3-FDYH]. ↑
- .Id. ↑
- .Id. ↑
- .See, e.g., Mark S. Ellis, The Changing Legal Standards for the War in Gaza, Huffington Post (Aug. 21, 2014), https://www.huffingtonpost.com/mark-s-ellis-/the-changing-legal-standa_b_5697496.html [https://perma.cc/E9AJ-XKJL] (claiming that “Israel has a greater legal duty to adhere to a higher proportionality standard because of its unique defensive stature”). The United Nations Independent Commission of Inquiry on the 2014 Gaza Conflict noted that civilians were able to heed rocket attack warnings by moving to areas where Iron Dome provided protection. Rep. of the Detailed Findings of the Comm’n of Inquiry on the 2014 Gaza Conflict, ¶ 95, UN Doc. A/HRC/29/CRP.4 (June 24, 2015). ↑
- .See, e.g., Súsanna Jógvansdóttir Christiansen, Has the Iron Dome Changed the Legitimacy of Responding to Rocket Threats? 42 (Mar. 1, 2015) (unpublished M.A. thesis, Tel Aviv University), http://www.samfelagid.fo/media/1114/thesis-has-the-iron-dome-changed-the-legitimacy-of-responding-to-rocket-threats.pdf [https://perma.cc/C3U7-RZBJ] (noting that “the Iron Dome, even though improving security, does not eliminate the effect terror has upon a society”); Benjamin Wittes, Israeli Targeting Procedures and the Concept of Proportionality, Lawfare (Dec. 15, 2015), https://www.lawfareblog.com/israeli-targeting-procedures-and-concept-proportionality [https://perma.cc/N47Z-BT27] (“If it weren’t for the Iron Dome missile defense system, . . . the aggregate casualty numbers on the Israeli side would be far higher than they are. And it’s a little perverse to argue that strong civilian defense renders otherwise appropriate offensive operations disproportionate because one side isn’t losing enough people.”). ↑
- .Elizabeth M. Bartels, Is Iron Dome a Poisoned Chalice?: Strategic Risks from Tactical Success, Strategy Bridge (Nov. 29, 2017), https://thestrategybridge.org/thebridge/2017/11/29
/is-iron-dome-a-poisoned-chalice-strategic-risks-from-tactical-success [https://perma.cc/J7Y7-G3QR]. ↑
- .E.g., Geneva Convention for the Amelioration of the Condition of the Wounded and Sick in Armed Forces in the Field, Aug. 12, 1949, 6 U.S.T. 3114, 75 U.N.T.S. 31; Geneva Convention for the Amelioration of the Condition of Wounded, Sick and Shipwrecked Members of Armed Forces at Sea, Aug. 12, 1949, 6 U.S.T. 3217, 75 U.N.T.S. 85; Geneva Convention Relative to the Treatment of Prisoners of War, Aug. 12, 1949, 6 U.S.T. 3316, 75 U.N.T.S. 135; Geneva Convention Relative to the Protection of Civilian Persons in Time of War, Aug. 12, 1949, 6 U.S.T. 3516, 75 U.N.T.S. 287. ↑
- .Protocol Additional to the Geneva Conventions of 12 August 1949, and Relating to the Protection of Victims of International Armed Conflicts art. 48, June 8, 1977, 1125 U.N.T.S. 3 [hereinafter Additional Protocol I]. ↑
- .Other treaty obligations that pertain to defense refer to the protections and immunities that parties must accord to civil defense units, which their counterparty might deploy for the amelioration of harm among that counterparty’s own civilian population. E.g., id. art. 65. Article 61 of Additional Protocol I lists the humanitarian tasks that civil defense units should be engaged in, including warning, evacuation, management of shelters, rescue, medical aid, and others. Id. art. 61. There is, however, no obligation on any party to deploy such civil defense units in the first place, and whether or not such units are raised or deployed is a matter of choice for the parties concerned. ↑
- .Id. art. 58. ↑
- .Int’l Comm. of the Red Cross, Commentary on the Additional Protocols of 8 June 1977 to the Geneva Conventions of 12 August 1949, at 692 (Yves Sandoz, Christophe Swinarski & Bruno Zimmerman eds., 1987). ↑
- .Id. ↑
- .Id. ↑
- .Id. ↑
- .See, e.g., Additional Protocol I, supra note 80, art. 51, ¶ 5 (allowing for “incidental loss of civilian life, injury to civilians, damage to civilian objects, or a combination thereof” that is not “excessive in relation to the concrete and direct military advantage anticipated”). ↑
- .See, e.g., id. art. 57, ¶ 1 (“In the conduct of military operations, constant care shall be taken to spare the civilian population, civilians and civilian objects.”). ↑
- .E.g., David Luban, Just War and Human Rights, 9 Phil. & Pub. Aff. 160, 175 (1980); Iddo Porat & Ziv Bohrer, Preferring One’s Own Civilians: May Soldiers Endanger Enemy Civilians More Than They Would Endanger Their State’s Civilians?, 47 Geo. Wash. Int’l L. Rev. 99, 158 (2015); Asa Kasher & Amos Yadlin, ‘Israel & the Rules of War’: An Exchange, N.Y. Rev. Books (June 11, 2009), http://www.nybooks.com/articles/2009/06/11/israel-the-rules-of-war-an-exchange/ [https://perma.cc/5XRM-G7BN]; Avishai Margalit & Michael Walzer, Israel: Civilians and Combatants, N.Y. Rev. Books (May 14, 2009), https://www.nybooks.com/articles/2009/05/14
/israel-civilians-combatants/ [https://perma.cc/ZX7Z-JJKP]. ↑
- .Schmitt & Merriam, supra note 9, at 127. ↑
- .Id. at 126. ↑
- .Id. ↑
- .Amichai Cohen & Yuval Shany, Contextualizing Proportionality Analysis? A Response to Schmitt and Merriam on Israel’s Targeting Practices, Just Security (May 7, 2015), https://www.justsecurity.org/22786/contextualizing-proportionality-analysis-response-schmitt-merriam/ [https://perma.cc/8EXR-C43F]. ↑
- .In their article on Iron Dome, Daphné Richemond-Barak and Ayal Feinberg also recognize the effects of Iron Dome on the reduction of civilian casualties on both sides. Richemond-Barak & Feinberg, supra note 16, at 474. They raise different concerns about the possible drawbacks of the system, mainly in terms of inviting further escalation by Hamas. Id. at 482. They do not address the possible disincentives for investment in defense that derive from increasing the constraints on Israel’s freedom of action against Hamas. ↑
- .The symmetric-defenses case is analyzed in Part V below. Naturally, in almost no case are defenses either completely asymmetric or completely symmetric in the sense of zero investment in defense in the former case or equal investment in defense in the latter. We use “asymmetric” and “symmetric” as mere approximations of the extreme ends of the spectrum. ↑
- .Again, we concede that civilian welfare is not the only value that the international laws of war seek to protect and promote; other values such as states’ survival or self-determination might require a great deal of sacrifice of civilian welfare. Still, for the reasons stated above, we assume that civilian welfare is at least a central and significant aim of the law. ↑
- .See supra subpart I(A). ↑
- .Our focus on the agency problem on B’s side does not mean that there can be no agency problem on A’s side. Indeed, there will likely be agency problems on both sides. ↑
- .We recognize that parties may not strictly adhere to the law; in such cases, the effects of international law that we identify will be weaker. ↑
- .Again, there may be other values at stake, but for the reasons we outline in the Introduction, we focus here on civilian lives. ↑
- .We make no assumption here about B’s compliance with the law. Even within the bounds of permissible attacks, there is a range of possible intensity. ↑
- .In the real world, we observe multiple rounds of attacks and counterattacks. Yet, as will be demonstrated below, this three-period framework is sufficiently rich to capture the essence of the strategic interaction between Israel and Hamas. ↑
- .In the Iron Dome example, a larger number of civilian casualties increases the probability that Israel will launch a retaliatory attack as well as the severity of this attack, and a smaller number of civilian casualties reduces the likelihood and severity of a retaliatory attack. ↑
- .On the general agency problem between the government and the citizenry, see José Mariá Maravall, Accountability and Manipulation, in Democracy, Accountability, and Representation 154 (Adam Przeworski, Susan C. Stokes & Bernard Manin eds., 1999). There is reason to believe that the agency problem is less severe in a functioning democracy. See id. at 156 (“There is substantial comparative empirical evidence that elections do indeed influence policy prospectively . . . .”); James A. Stimson, Michael B. Mackuen & Robert S. Erikson, Dynamic Representation, 89 Am. Pol. Sci. Rev. 543, 559 (1995) (observing that American politicians are responsive to public opinion). In the context of the Israel–Hamas conflict, Hamas may be a perfectly faithful agent of the Palestinian civilians in Gaza who believe that harming Israel will produce a more favorable political outcome. Or Hamas might be an imperfect agent—harming Israel for its own political benefit or not fully internalizing the harm to Palestinian civilians. Similarly, the Israeli government can be a more or less faithful agent of Israeli civilians. ↑
- .Again, recall that IHL would seek to minimize harm to civilians even where there is a just cause for the war and the war meets the overall conditions of necessity and proportionality. ↑
- .In the context of the Israel–Hamas conflict, Israel may well care about minimizing civilian casualties on the Palestinian side—either for humanitarian reasons or to avoid international condemnation. ↑
- .See infra sections III(C)(5), III(D)(5). ↑
- .For a general introduction to the game-theoretic concepts of “extensive form games” and “backward induction,” see, for example, Drew Fudenberg & Jean Tirole, Game Theory 72–83 (1991). ↑
- .We assume that, irrespective of legal constraints, the harshness of a retaliatory action is correlated, at least to some degree, with the harm suffered with the initial strike. ↑
- .The analysis in the text considers B’s decision about the intensity of the T1 attack as compared to a “no attack” benchmark. We can easily extend the analysis to allow for two different attack types (e.g., in the context of the Israel–Hamas conflict, firing rockets vs. digging infiltration tunnels). In this extended framework, B chooses how to allocate resources between the two modes of attack, and A’s decision to defend against one mode of attack will cause B to shift resources to the other mode. ↑
- .This statement should be qualified: A may care about minimizing harm to B’s civilian population. If so, the benefit that A gets from attacking B would be smaller. ↑
- .Kamm, supra note 73. ↑
- .Since the law is designed to help B, we focus on the law’s effect on B—specifically, on how well the law addresses the positive-externality problem. A more complete assessment would also consider the law’s effect on A. A stricter law constrains A, limits its ability to retaliate, and thus hurts A. The law is normatively justified if the cost to A is outweighed by the benefit to B, all in terms of civilian lives. ↑
- .See supra section II(A)(2). This, again, assumes that the threat is sufficiently concrete and imminent to justify force in self-defense. ↑
- .See generally Herbert A. Simon, Rational Choice and the Structure of the Environment, 63 Psychol. Rev. 129 (1956) (introducing satisficing theory). ↑
- .Richemond-Barak & Feinberg, supra note , at 519–25. ↑
- .Raphael S. Cohen et al., From Cast Lead to Protective Edge: Lessons from Israel’s Wars in Gaza 165–67 (2017), https://www.rand.org/content/dam/rand/pubs/research
_reports/RR1800/RR1888/RAND_RR1888.pdf [https://perma.cc/8GD5-NPH8]. ↑
- .Richemond-Barak & Feinberg, supra note 16, at 484. ↑
- .Id. at 488. During Operation Protective Edge, Israel eventually launched a ground assault, but that assault targeted Hamas’s infiltration tunnels, not the rocket launchers. Id. ↑
- .Id. at 484–85; Cohen et al., supra note , at 167. ↑
- .Cohen et al., supra note , at 65–66. ↑
- .Id. at 166. ↑
- .Yoav Fromer, The Missiles Keeping Israel Safe May Do More Long-Term Harm than Good, Wash. Post (July 14, 2014), https://www.washingtonpost.com/posteverything/wp/2014/
07/14/the-missiles-keeping-israel-safe-may-do-more-long-term-harm-than-good/ [https://perma.cc/NDS9-KDH3]; Griff Witte & Ruth Eglash, Iron Dome, Israel’s Antimissile System, Changes Calculus of Fight with Hamas, Wash. Post (July 14, 2014), https://www.washingtonpost.com/world/middle_east/israel-shoots-down-hamas-drone/2014/07/14/991c46da-0b47-11e4-b8e5-d0de80767fc2_story.html [https://perma.cc/982L-RQWK] (paraphrasing Amir Peretz, former Israeli defense minister, saying “In the end, the only thing that will bring true quiet is a diplomatic solution”); see also Jack Khoury, Who Needs a Peace Deal when Israel Has Iron Dome?, Haaretz (July 13, 2014), https://www.haaretz.com/israel-news/.premium-1.604760 [https://perma.cc/Y6Z3-M29T] (sarcastically illustrating this point). ↑
- .How Israel’s “Iron Dome” Works, Economist (July 16, 2014), https://www.economist
.com/blogs/economist-explains/2014/07/economist-explains-12 [https://perma.cc/BM7N-L7WA]. ↑
- .For a contrary view on Iron Dome’s potential contribution to peace, see 60 Minutes: Will Israel’s “Iron Dome” Help Bring Peace? (CBS News television broadcast Feb. 17, 2013), https://www.cbsnews.com/news/will-israels-iron-dome-help-bring-peace/ [https://perma.cc/9VB4-QRB3] (claiming that Ehud Barak, then Israeli Minister of Defense, argued “that if Iron Dome makes Israelis feel more secure, less threatened, they’ll be more willing to make peace with the Palestinians”). ↑
- .Richemond-Barak & Feinberg, supra note 16, at 486–87. ↑
- .Cohen et al., supra note 117, at 166. ↑
- .Id. ↑
- .Bartels, supra note 78. ↑
- .1972 ABM Treaty, supra note 36. ↑
- .See, e.g., Tucker Higgins, North Korean Missile Lands in Sea of Japan, Pentagon Says, CNBC (Nov. 28, 2017), http://www.cnbc.com/2017/11/28/north-korea-fires-ballistic-missile-report.html [https://perma.cc/ZJ4J-K63D] (reporting on a North Korean ballistic missile test); Claire Phipps & Graham Russell, North Korea: Ballistic Missile Launched Over Japan – As It Happened, Guardian (Sept. 15, 2017), https://www.theguardian.com/world/live/2017/sep/15/
north-korea-launches-missile-over-japan-live-updates [https://perma.cc/88SC-JD9Q] (same); Chris Sanders, U.S. Approves Anti-ballistic Missile Sale to Japan amid North Korea Threat, Reuters (Jan. 9, 2018), https://www.reuters.com/article/us-raytheon-pentagon-japan/u-s-approves-anti-ballistic-missile-sale-to-japan-amid-north-korea-threat-idUSKBN1EY2U5 [https://perma.cc/X9CL-G5Q5] (reporting on new sales of antiballistic missiles in response to North Korea). ↑
- .In technical terms, we know that the reaction functions are increasing, namely—that their first derivative is positive: and . The question is whether their second derivative is positive, i.e., and , or negative, i.e., and . (It is also possible that the derivative is positive for one party and negative for the other.) ↑
- .Cf. Gordon Tullock, Efficient Rent Seeking, in Toward a Theory of the Rent-Seeking Society 97, 99–104 (James M. Buchanan, Robert D. Tollison & Gordon Tullock eds., 1980). In this classic contest model, a similar, high-investment equilibrium obtains. The standard interpretation of the Tullock model, and of similar contest models, focuses on offensive, rather than defensive, investments. For more on contest models, see Kai A. Konrad, Strategy and Dynamics in Contests 42–43 (2009); Derek J. Clark & Kai A. Konrad, Contests with Multi-tasking, 109 Scandinavian J. Econ. 303, 305 (2007); Erik O. Kimbrough, Kevin Laughren & Roman Sheremeta, War and Conflict in Economics: Theories, Applications, and Recent Trends, J. Econ. Behav. & Org. (forthcoming); Kai A. Konrad, Spatial Contests, 18 Int’l J. Indus. Org. 965, 966 (2000); and Kai A. Konrad, Trade Contests, 51 J. Int’l Econ. 317, 319 (2000). ↑
- .In the asymmetric-defenses case (Part III), A’s defenses affected the intensity of B’s attack. This notion of the intensity of an attack is different from the offensive response that we are referring to here. The analysis in Part III assumed a given level of offensive capabilities. Here we consider ex ante investments that increase a party’s offensive capabilities. ↑
- . Eugene Rumer, Farewell to Arms . . . Control, Carnegie Endowment for Int’l Peace (Apr. 17, 2018), https://carnegieendowment.org/2018/04/17/farewell-to-arms-.-.-.-control-pub-76088 [https://perma.cc/P7SY-HTUS]. ↑
- .E.g., John Lewis Gaddis, The United States and the End of the Cold War: Implications, Reconsiderations, Provocations 44 & 225 n.83 (1992). ↑
- .See Rich, supra note 3 (discussing South Korea’s possible future use of the THAAD system). ↑